Refer to the exhibit. An administrator configures four switches for local authentication using passwords that are stored as a cryptographic hash. The four switches must also support SSH access for administrators to manage the network infrastructure. Which switch is configured correctly to meet these requirements?
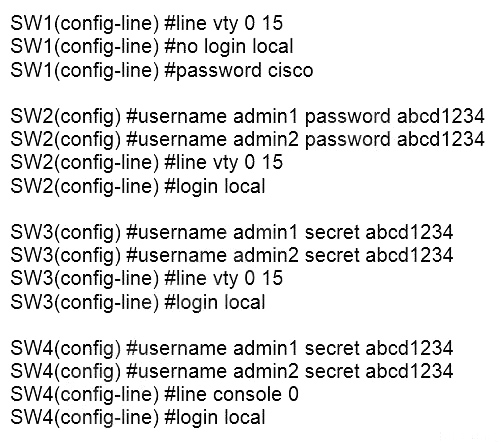
A. SW1
B. SW2
C. SW3
D. SW4

A. SW1
B. SW2
C. SW3
D. SW4