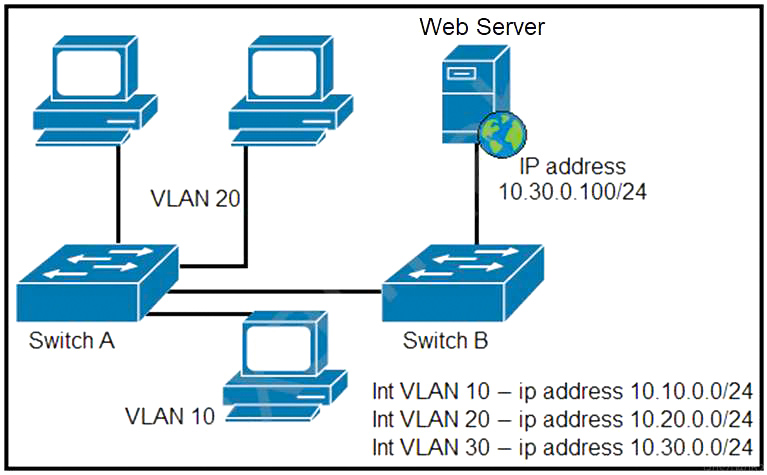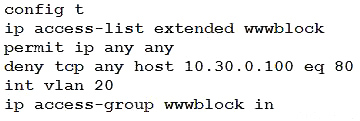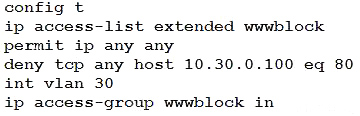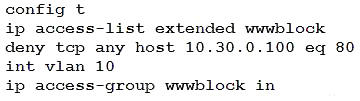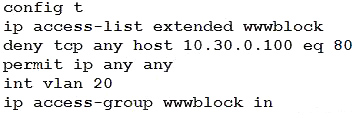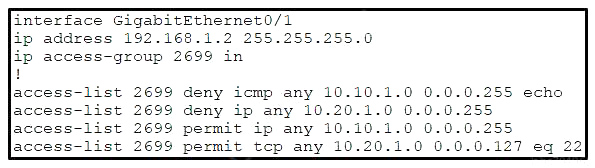
Refer to the exhibit. A network administrator must permit SSH access to remotely manage routers in a network.
The operations team resides on the 10.20.1.0/25 network. Which command will accomplish this task?
A. access-list 2699 permit udp 10.20.1.0 0.0.0.255
B. no access-list 2699 deny tcp any 10.20.1.0 0.0.0.127 eq 22
C. access-list 2699 permit tcp any 10.20.1.0 0.0.0.255 eq 22
D. no access-list 2699 deny ip any 10.20.1.0 0.0.0.255