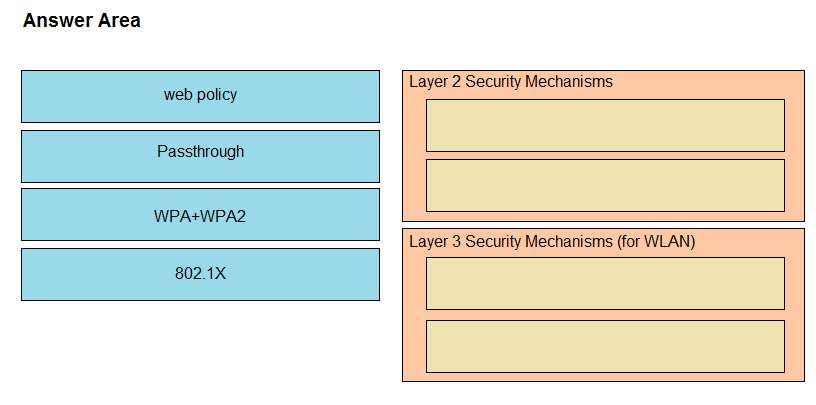
Refer to the exhibit. An extended ACL has been configured and applied to router R2. The configuration failed to work as intended.
Which two changes stop outbound traffic on TCP ports 25 and 80 to 10.0.20.0/26 from the 10.0.10.0/26 subnet while still allowing all other traffic? (Choose two.)
A. Add a "permit ip any any" statement at the end of ACL 101 for allowed traffic.
B. Add a "permit ip any any" statement to the beginning of ACL 101 for allowed traffic.
C. The ACL must be moved to the Gi0/1 interface outbound on R2.
D. The source and destination IPs must be swapped in ACL 101.
E. The ACL must be configured the Gi0/2 interface inbound on R1.