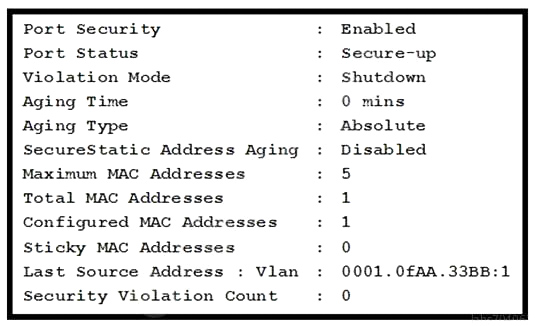
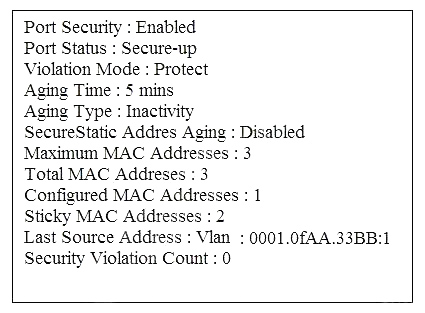
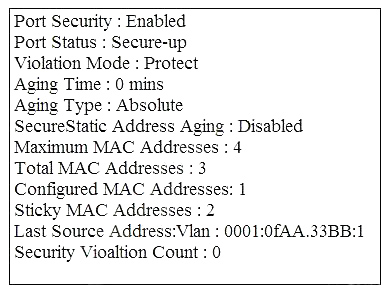
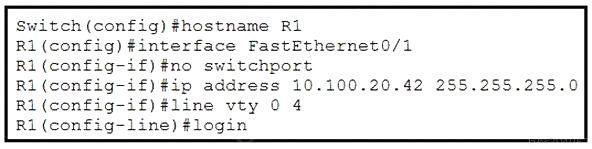
Refer to the exhibit. What is the effect of this configuration?
A. The switch port remains administratively down until the interface is connected to another switch.
B. Dynamic ARP Inspection is disabled because the ARP ACL is missing.
C. The switch port interface trust state becomes untrusted.
D. The switch port remains down until it is configured to trust or untrust incoming packets.