E-mail traffic from the Internet is routed via firewall-1 to the mail gateway. Mail is routed from the mail gateway, via firewall-2, to the mail recipients in the internal network. Other traffic is not allowed. For example, the firewalls do not allow direct traffic from the
Internet to the internal network.
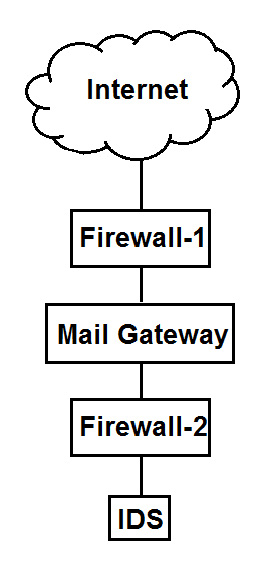
The intrusion detection system (IDS) detects traffic for the internal network that did not originate from the mail gateway. The FIRST action triggered by the IDS should be to:
A. alert the appropriate staff.
B. create an entry in the log.
C. close firewall-2.
D. close firewall-1.
Internet to the internal network.

The intrusion detection system (IDS) detects traffic for the internal network that did not originate from the mail gateway. The FIRST action triggered by the IDS should be to:
A. alert the appropriate staff.
B. create an entry in the log.
C. close firewall-2.
D. close firewall-1.