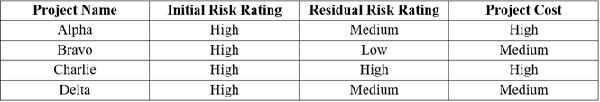
Which of the following will BEST support management reporting on risk?
A. A risk register.
B. Key performance indicators.
C. Control self-assessment.
D. Risk policy requirements.
A. A risk register.
B. Key performance indicators.
C. Control self-assessment.
D. Risk policy requirements.