After a high-profile systems breach at an organization’s key vendor, the vendor has implemented additional mitigating controls. The vendor has voluntarily shared the following set of assessments:
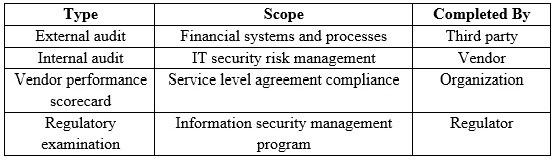
Which of the assessments provides the MOST reliable input to evaluate residual risk in the vendor’s control environment?
A. External audit
B. Internal audit
C. Vendor performance scorecard
D. Regulatory examination

Which of the assessments provides the MOST reliable input to evaluate residual risk in the vendor’s control environment?
A. External audit
B. Internal audit
C. Vendor performance scorecard
D. Regulatory examination