As per RFC, The DoD TCP/IP protocol model defines four layers, with the layers having names, not numbers, as follows:
Application (process-to-process) Layer: This is the scope within which applications create user data and communicate this data to other processes or applications on another or the same host. The communications partners are often called peers. This is where the “higher level” protocols such as SMTP, FTP, SSH, HTTP, etc. operate.
Transport (host-to-host) Layer: The Transport Layer constitutes the networking regime between two network hosts, either on the local network or on remote networks separated by routers. The Transport Layer provides a uniform networking interface that hides the actual topology (layout) of the underlying network connections. This is where flow-control, error-correction, and connection protocols exist, such as TCP. This layer deals with opening and maintaining connections between internet hosts.
Internet (internetworking) Layer: The Internet Layer has the task of exchanging datagrams across network boundaries. It is therefore also referred to as the layer that establishes internetworking; indeed, it defines and establishes the Internet. This layer defines the addressing and routing structures used for the TCP/IP protocol suite. The primary protocol in this scope is the Internet Protocol, which defines IP addresses. Its function in routing is to transport datagrams to the next IP router that has the connectivity to a network closer to the final data destination.
Link (network access) Layer: This layer defines the networking methods with the scope of the local network link on which hosts communicate without intervening routers. This layer describes the protocols used to describe the local network topology and the interfaces needed to affect transmission of Internet Layer datagrams to next-neighbor hosts.
The DoD tcp/ip model DoD model Osi Model
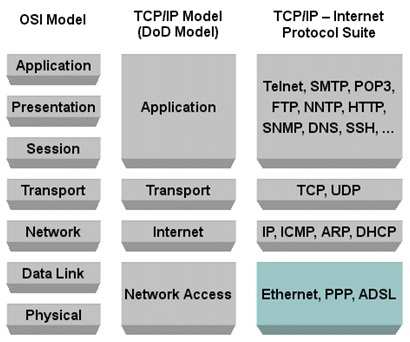
Graphic above from:
http://bit.kuas.edu.tw/
REALITY VERSUS THE STANDARD In real life today, this is getting very confusing. Many books and references will not use exactly the same names as the initial RFC that was published. For example, the Link layer is often times called Network Access. The same applies with Transport which is often times called Host-to-Host and vice versa.
The following answer is incorrect: The session layer is defined within the OSI/ISO model but not within the DOD model. Being incorrect it made it the best answer according to the question. It does not belong to the DoD TCP/IP Model.
Reference(s) Used for this question:
http://www.freesoft.org/CIE/RFC/1122/ http://bit.kuas.edu.tw/~csshieh/teach/np/tcpip/