A company is using an AWS CodeBuild project to build and package an application. The packages are copied to a shared Amazon S3 bucket before being deployed across multiple AWS accounts.
The buildspec.yml file contains the following:
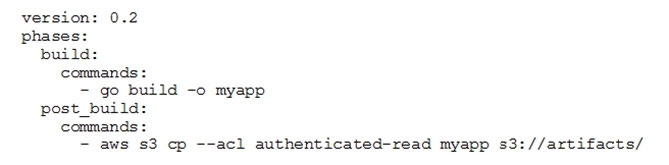
The DevOps Engineer has noticed that anybody with an AWS account is able to download the artifacts.
What steps should the DevOps Engineer take to stop this?
A. Modify the post_buildto command to use –-acl public-readand configure a bucket policy that grants read access to the relevant AWS accounts only.
B. Configure a default ACL for the S3 bucket that defines the set of authenticated users as the relevant AWS accounts only and grants read-only access.
C. Create an S3 bucket policy that grants read access to the relevant AWS accounts and denies read access to the principal “*”
D. Modify the post_build command to remove –-acl authenticated-readand configure a bucket policy that allows read access to the relevant AWS accounts only.
The buildspec.yml file contains the following:

The DevOps Engineer has noticed that anybody with an AWS account is able to download the artifacts.
What steps should the DevOps Engineer take to stop this?
A. Modify the post_buildto command to use –-acl public-readand configure a bucket policy that grants read access to the relevant AWS accounts only.
B. Configure a default ACL for the S3 bucket that defines the set of authenticated users as the relevant AWS accounts only and grants read-only access.
C. Create an S3 bucket policy that grants read access to the relevant AWS accounts and denies read access to the principal “*”
D. Modify the post_build command to remove –-acl authenticated-readand configure a bucket policy that allows read access to the relevant AWS accounts only.