A Developer accesses AWS CodeCommit over SSH. The SSH keys configured to access AWS CodeCommit are tied to a user with the following permissions:
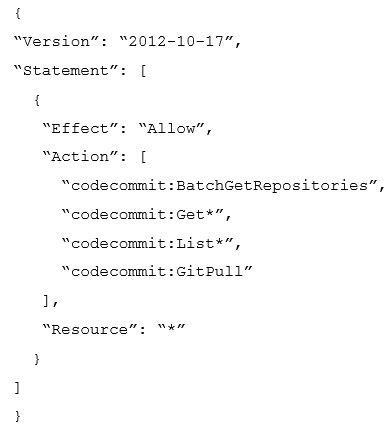
The Developer needs to create/delete branches.
Which specific IAM permissions need to be added, based on the principle of least privilege?
A. “codecommit:CreateBranch” “codecommit:DeleteBranch”
B. “codecommit:Put*”
C. “codecommit:Update*”
D. “codecommit:*”

The Developer needs to create/delete branches.
Which specific IAM permissions need to be added, based on the principle of least privilege?
A. “codecommit:CreateBranch” “codecommit:DeleteBranch”
B. “codecommit:Put*”
C. “codecommit:Update*”
D. “codecommit:*”