Application developers are reporting Access Denied errors when trying to list the contents of an Amazon S3 bucket by using the IAM user “arn:aws:iam::111111111111:user/application”. The following S3 bucket policy is in use:
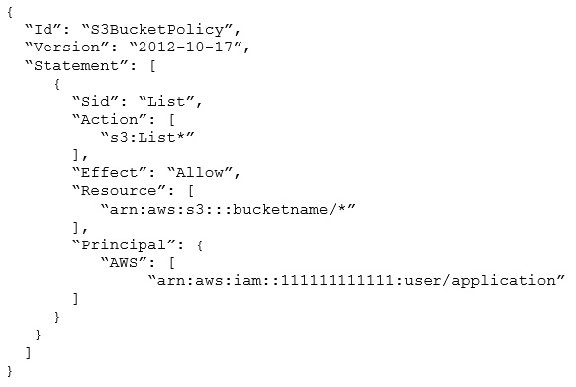
How should a SysOps Administrator modify the S3 bucket policy to fix the issue?
A. Change the “Effect” from “Allow” to “Deny”
B. Change the “Action” from “s3:List*” to “s3:ListBucket”
C. Change the “Resource” from “arn:aws:s3:::bucketname/*” to “arn:aws:s3:::bucketname”
D. Change the “Principal” from “arn:aws:iam::111111111111:user/application” to “arn:aws:iam::111111111111:role/application”

How should a SysOps Administrator modify the S3 bucket policy to fix the issue?
A. Change the “Effect” from “Allow” to “Deny”
B. Change the “Action” from “s3:List*” to “s3:ListBucket”
C. Change the “Resource” from “arn:aws:s3:::bucketname/*” to “arn:aws:s3:::bucketname”
D. Change the “Principal” from “arn:aws:iam::111111111111:user/application” to “arn:aws:iam::111111111111:role/application”