A company has configured a library of IAM roles that grant access to various AWS resources. Each employee has an AWS IAM user, some of which have the permission to launch Amazon EC2 instances.
The SysOps Administrator has attached the following policy to those users:
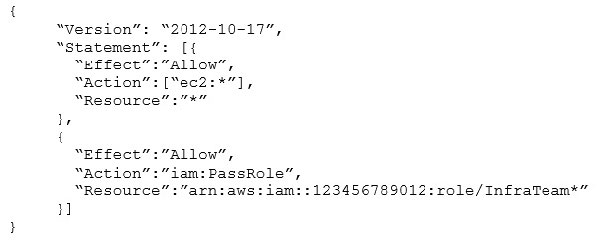
What would be the result of this policy?
A. Users are able to switch only to a role name that begins with “InfraTeam” followed by any other combination of characters.
B. Users with the role of InfraTeamLinux are able to launch an EC2 instance and attach that role to it.
C. “InfraTeam” role is being passed to a user who has full EC2 access.
D. EC2 instances that are launched by these users have full AWS permissions.
The SysOps Administrator has attached the following policy to those users:

What would be the result of this policy?
A. Users are able to switch only to a role name that begins with “InfraTeam” followed by any other combination of characters.
B. Users with the role of InfraTeamLinux are able to launch an EC2 instance and attach that role to it.
C. “InfraTeam” role is being passed to a user who has full EC2 access.
D. EC2 instances that are launched by these users have full AWS permissions.