A security analyst is reviewing the following Internet usage trend report:
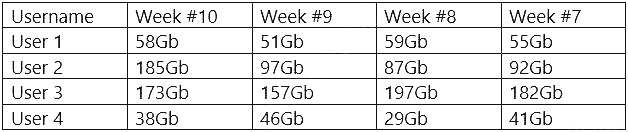
Which of the following usernames should the security analyst investigate further?
A. User 1
B. User 2
C. User 3
D. User 4

Which of the following usernames should the security analyst investigate further?
A. User 1
B. User 2
C. User 3
D. User 4