A security analyst at example.com receives SIEM alert for an IDS signature and reviews the associated packet capture and TCP stream:
Packet capture:
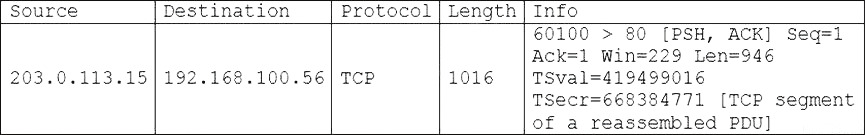
TCP stream:
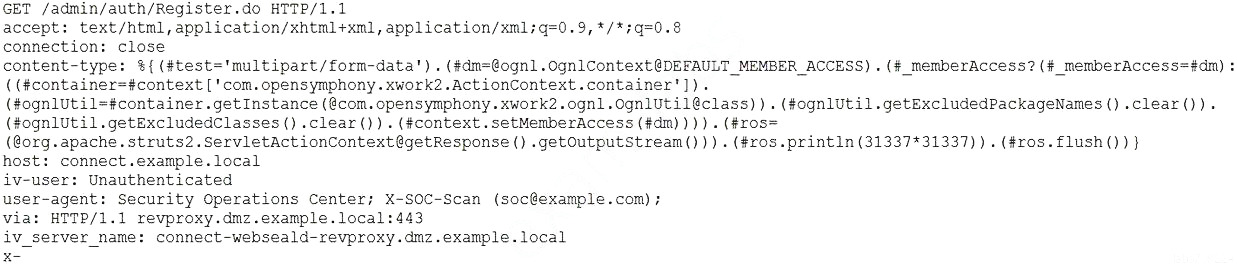
Which of the following actions should the security analyst take NEXT?
A. Review the known Apache vulnerabilities to determine if a compromise actually occurred.
B. Contact the application owner for connect.example.local for additional information.
C. Mark the alert as a false positive scan coming from an approved source.
D. Raise a request to the firewall team to block 203.0.113.15.
Packet capture:

TCP stream:

Which of the following actions should the security analyst take NEXT?
A. Review the known Apache vulnerabilities to determine if a compromise actually occurred.
B. Contact the application owner for connect.example.local for additional information.
C. Mark the alert as a false positive scan coming from an approved source.
D. Raise a request to the firewall team to block 203.0.113.15.