A security analyst discovers the following firewall log entries during an incident:
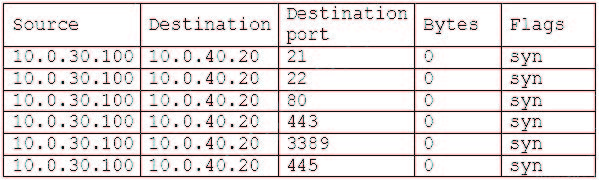
Which of the following is MOST likely occurring?
A. Banner grabbing
B. Port scanning
C. Beaconing
D. Data exfiltration

Which of the following is MOST likely occurring?
A. Banner grabbing
B. Port scanning
C. Beaconing
D. Data exfiltration