After an incident involving a phishing email, a security analyst reviews the following email access log:
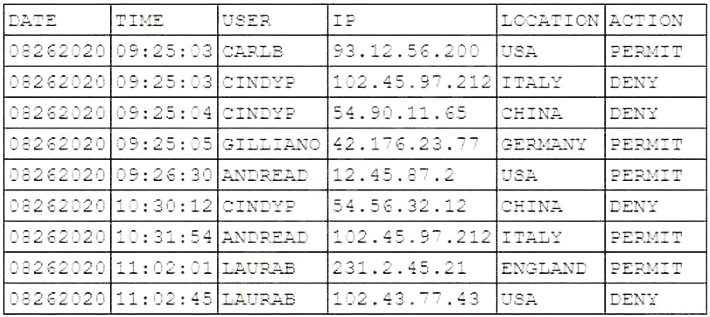
Based on this information, which of the following accounts was MOST likely compromised?
A. CARLB
B. CINDYP
C. GILLIANO
D. ANDREAD
E. LAURAB

Based on this information, which of the following accounts was MOST likely compromised?
A. CARLB
B. CINDYP
C. GILLIANO
D. ANDREAD
E. LAURAB