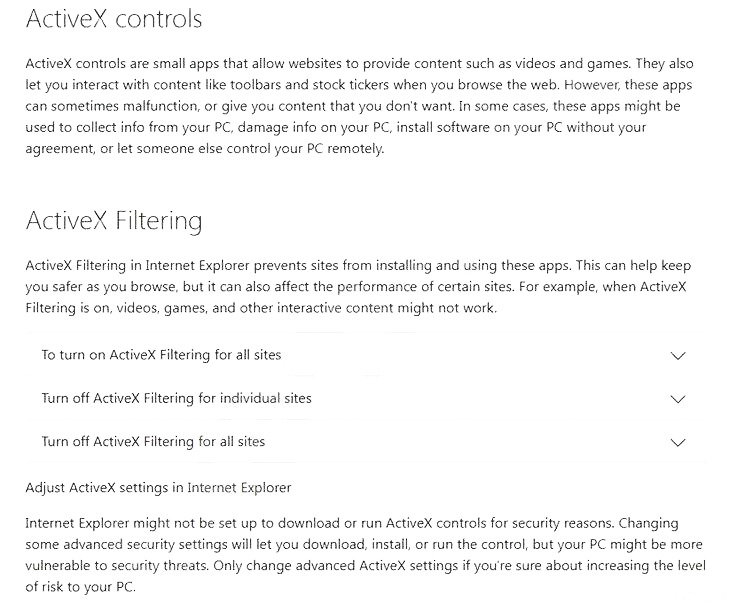
Which of the following is the BEST security practice to prevent ActiveX controls from running malicious code on a user's web application?
A. Deploying HIPS to block malicious ActiveX code
B. Installing network-based IPS to block malicious ActiveX code
C. Adjusting the web-browser settings to block ActiveX controls
D. Configuring a firewall to block traffic on ports that use ActiveX controls
A. Deploying HIPS to block malicious ActiveX code
B. Installing network-based IPS to block malicious ActiveX code
C. Adjusting the web-browser settings to block ActiveX controls
D. Configuring a firewall to block traffic on ports that use ActiveX controls