A security analyst is running a tool against an executable of an unknown source. The input supplied by the tool to the executable program and the output from the executable are shown below:
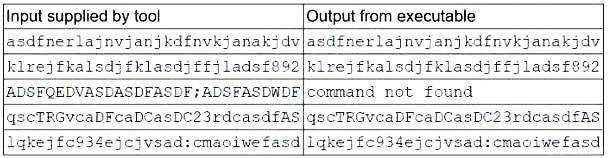
Which of the following should the analyst report after viewing this information?
A. A dynamic library that is needed by the executable is missing.
B. Input can be crafted to trigger an injection attack in the executable.
C. The tool caused a buffer overflow in the executable's memory.
D. The executable attempted to execute a malicious command.

Which of the following should the analyst report after viewing this information?
A. A dynamic library that is needed by the executable is missing.
B. Input can be crafted to trigger an injection attack in the executable.
C. The tool caused a buffer overflow in the executable's memory.
D. The executable attempted to execute a malicious command.