During routine monitoring, a security analyst identified the following enterprise network traffic:
Packet capture output:
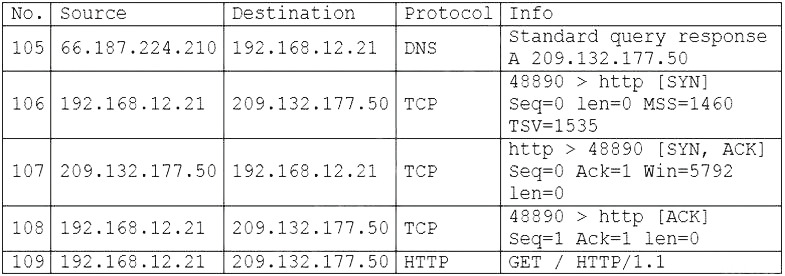
Which of the following BEST describes what the security analyst observed?
A. 66.187.224.210 set up a DNS hijack with 192.168.12.21.
B. 192.168.12.21 made a TCP connection to 66.187.224.210.
C. 192.168.12.21 made a TCP connection to 209.132.177.50.
D. 209.132.177.50 set up a TCP reset attack to 192.168.12.21.
Packet capture output:

Which of the following BEST describes what the security analyst observed?
A. 66.187.224.210 set up a DNS hijack with 192.168.12.21.
B. 192.168.12.21 made a TCP connection to 66.187.224.210.
C. 192.168.12.21 made a TCP connection to 209.132.177.50.
D. 209.132.177.50 set up a TCP reset attack to 192.168.12.21.