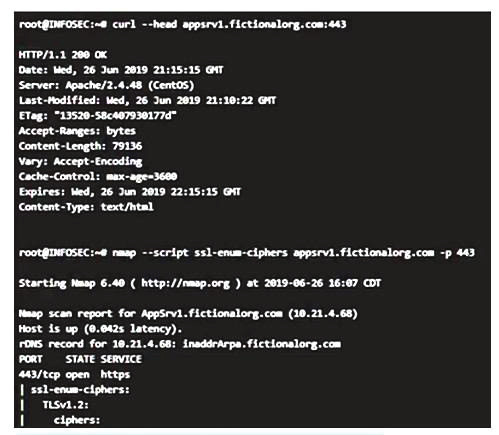
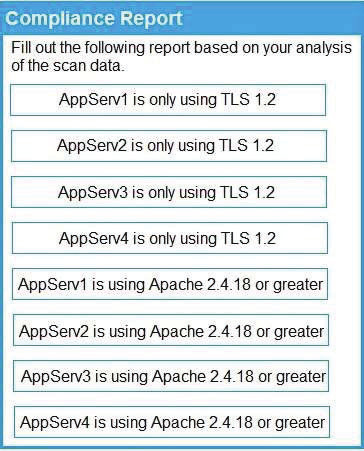
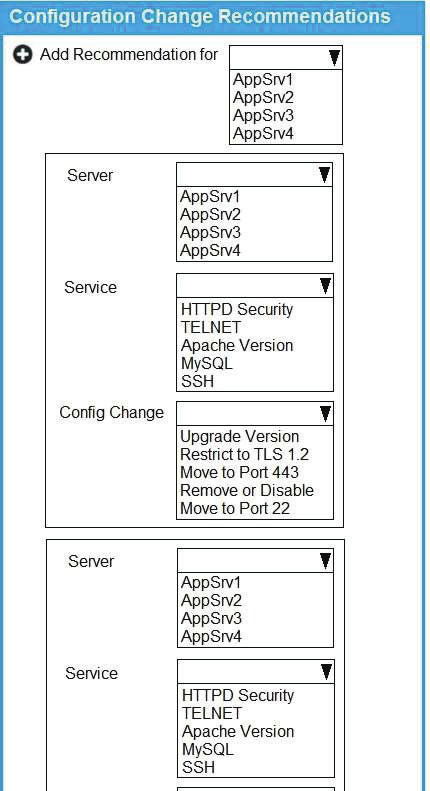
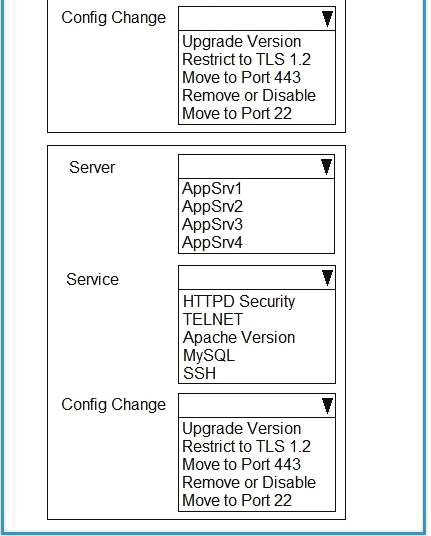
A security analyst reviews SIEM logs and detects a well-known malicious executable running in a Windows machine. The up-to-date antivirus cannot detect the malicious executable. Which of the following is the MOST likely cause of this issue?
A. The malware fileless and exists only in physical memory.
B. The malware detects and prevents its own execution in a virtual environment
C. The antivirus does not have the malware's signature.
D. The malware is being executed with administrative privileges.
A. The malware fileless and exists only in physical memory.
B. The malware detects and prevents its own execution in a virtual environment
C. The antivirus does not have the malware's signature.
D. The malware is being executed with administrative privileges.