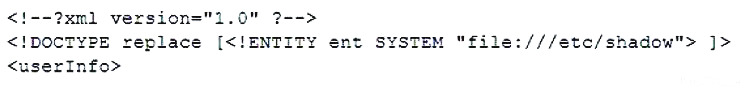
A security analyst identified one server that was compromised and used as a data mining machine, and a clone of the hard drive that was created. Which of the following will MOST likely provide information about when and how the machine was compromised and where the malware is located?
A. System timeline reconstruction
B. System registry extraction
C. Data carving
D. Volatile memory analysis
A. System timeline reconstruction
B. System registry extraction
C. Data carving
D. Volatile memory analysis