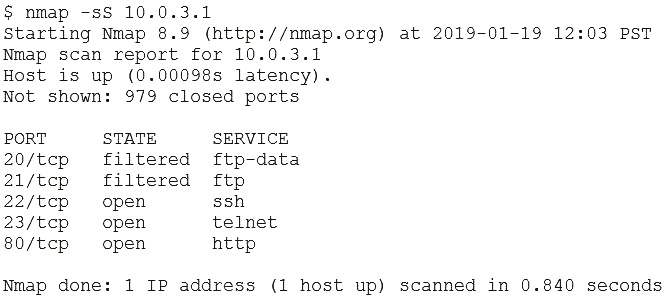
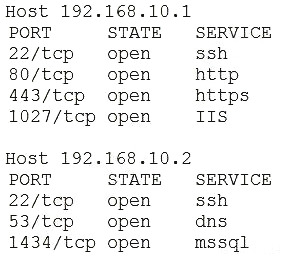
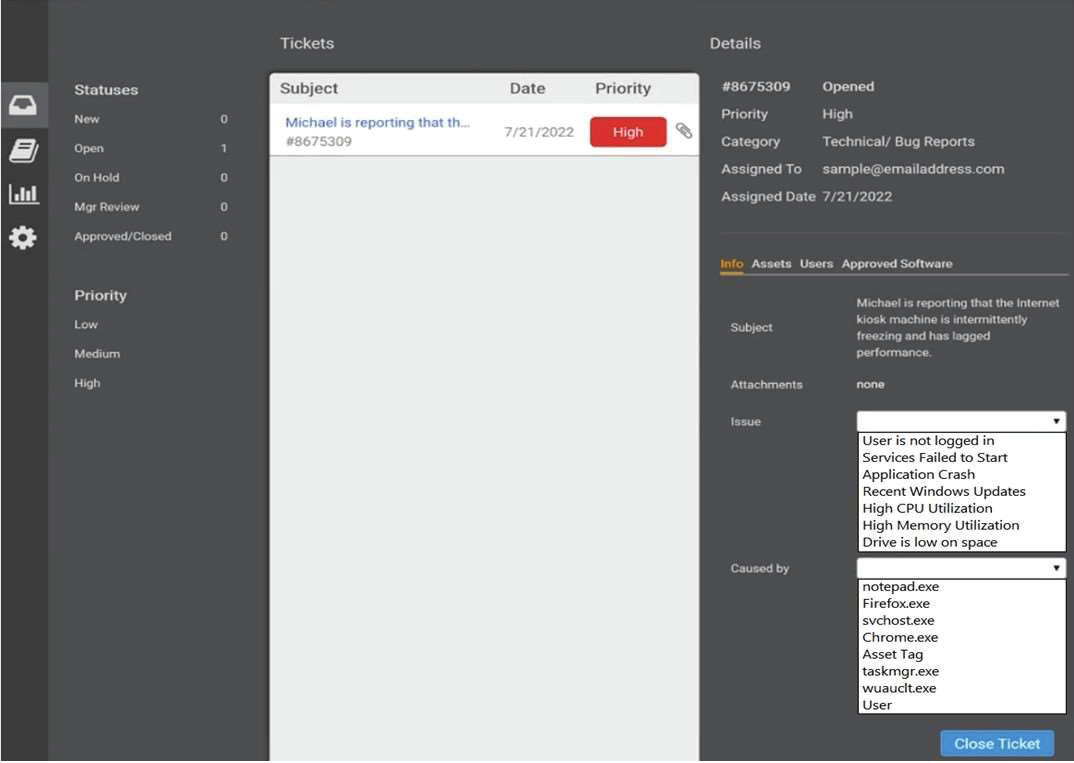
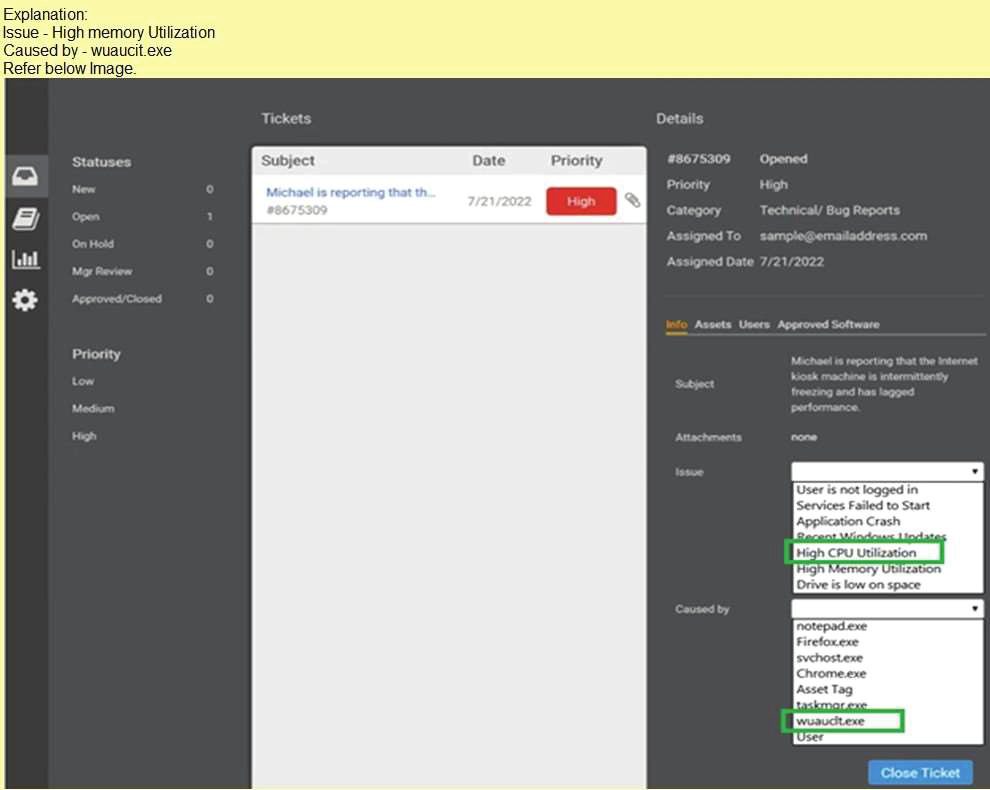
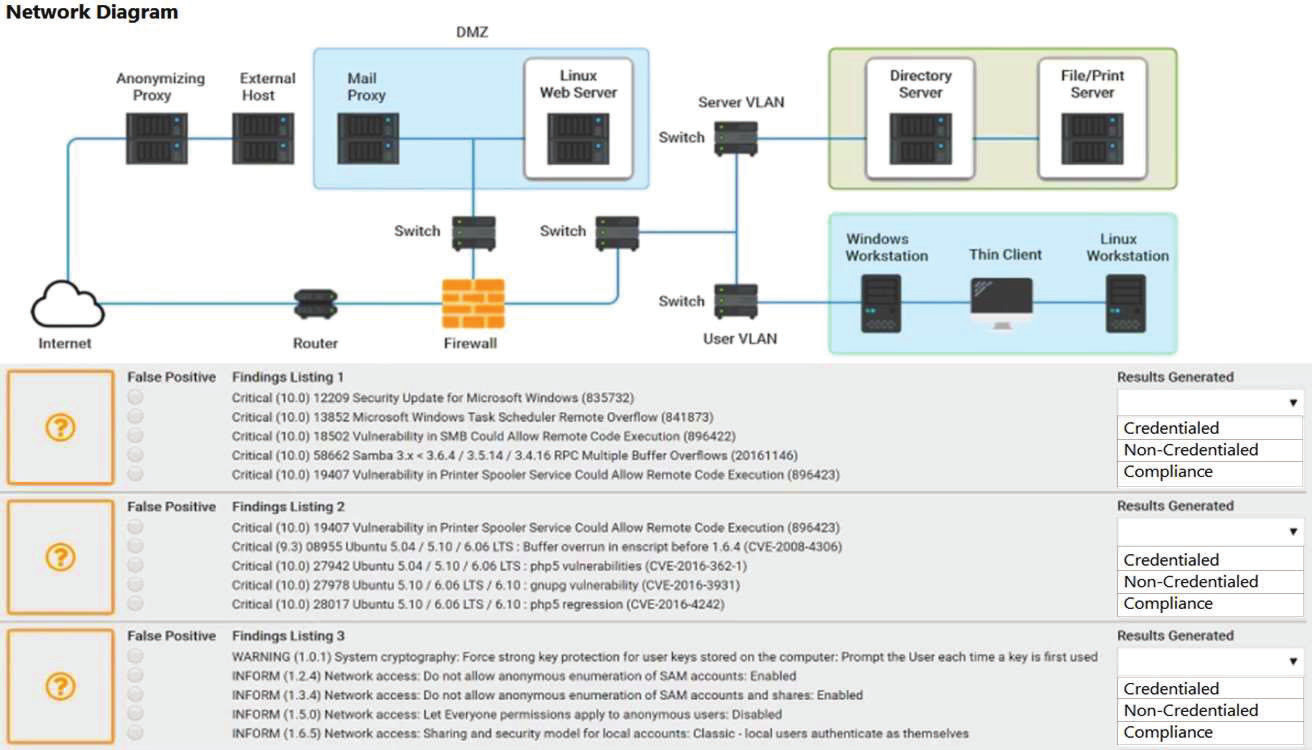
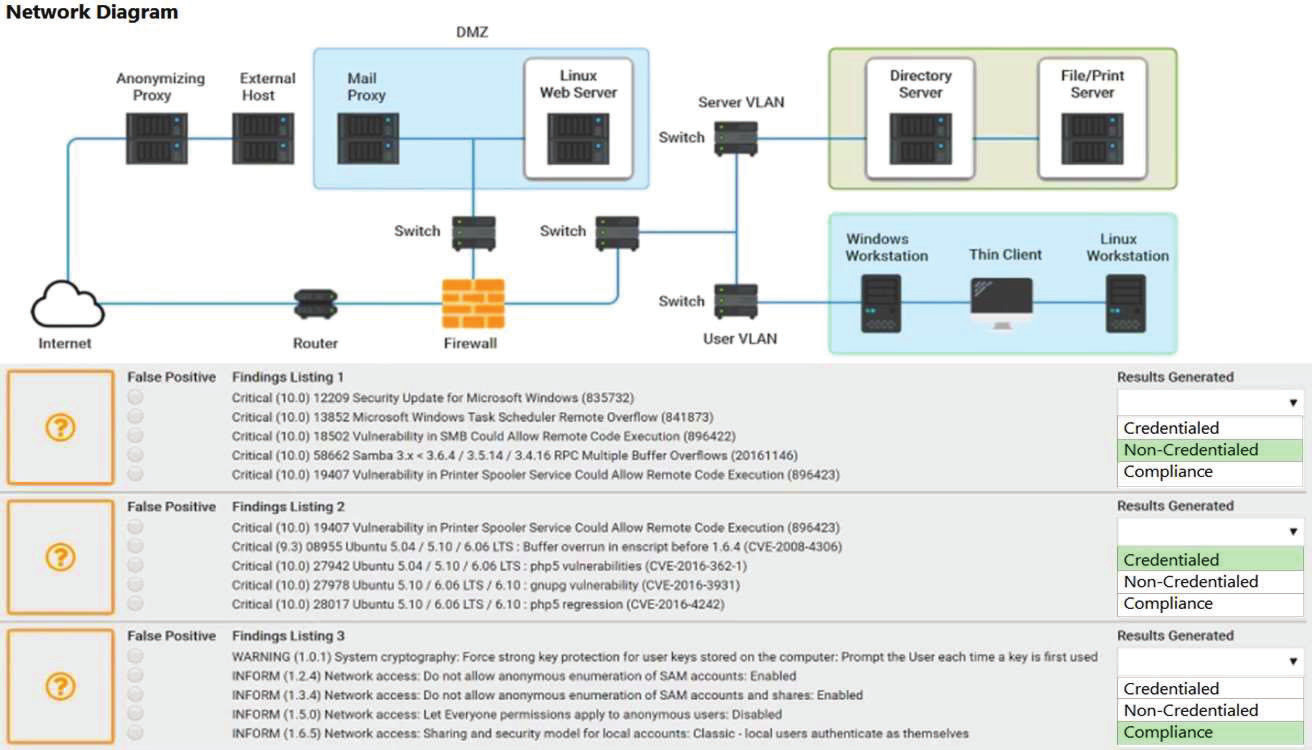
Due to continued support of legacy applications, an organization's enterprise password complexity rules are inadequate for its required security posture. Which of the following is the BEST compensating control to help reduce authentication compromises?
A. Smart cards
B. Multifactor authentication
C. Biometrics
D. Increased password-rotation frequency
A. Smart cards
B. Multifactor authentication
C. Biometrics
D. Increased password-rotation frequency