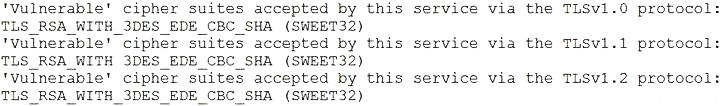
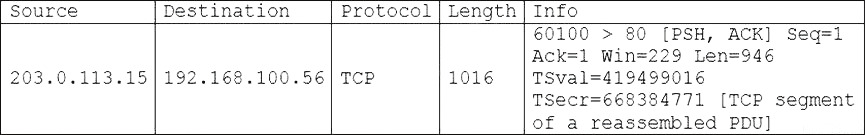
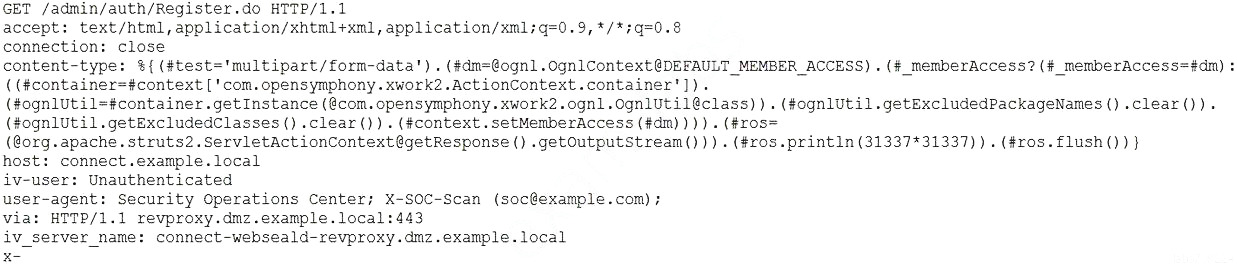
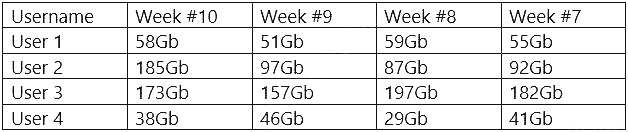
A security analyst needs to provide a copy of a hard drive for forensic analysis. Which of the following would allow the analyst to perform the task?
A. dcfldd if=/dev/one of=/mnt/usb/evidence.bin hash=md5, sha1 hashlog=/mnt/usb/ evidence.bin.hashlog
B. dd if=/dev/sda of=/mnt/usb/evidence.bin bs=4096; sha5l2sum /mnt/usb/ evidence.bin > /mnt/usb/evidence.bin.hash
C. tar -zcf /mnt/usb/evidence.tar.gz / -except /mnt; sha256sum /mnt/usb/ evidence.tar.gz > /mnt/usb/evidence.tar.gz.hash
D. find / -type f -exec cp {} /mnt/usb/evidence/ ; sha1sum /mnt/usb/evidence/* > /mnt/usb/evidence/evidence.hash
A. dcfldd if=/dev/one of=/mnt/usb/evidence.bin hash=md5, sha1 hashlog=/mnt/usb/ evidence.bin.hashlog
B. dd if=/dev/sda of=/mnt/usb/evidence.bin bs=4096; sha5l2sum /mnt/usb/ evidence.bin > /mnt/usb/evidence.bin.hash
C. tar -zcf /mnt/usb/evidence.tar.gz / -except /mnt; sha256sum /mnt/usb/ evidence.tar.gz > /mnt/usb/evidence.tar.gz.hash
D. find / -type f -exec cp {} /mnt/usb/evidence/ ; sha1sum /mnt/usb/evidence/* > /mnt/usb/evidence/evidence.hash