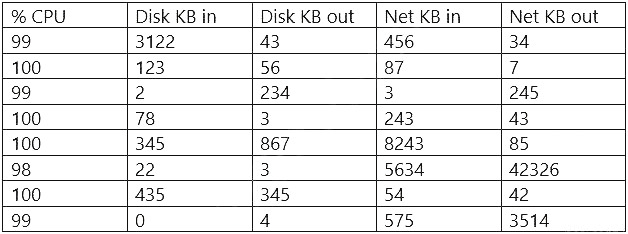
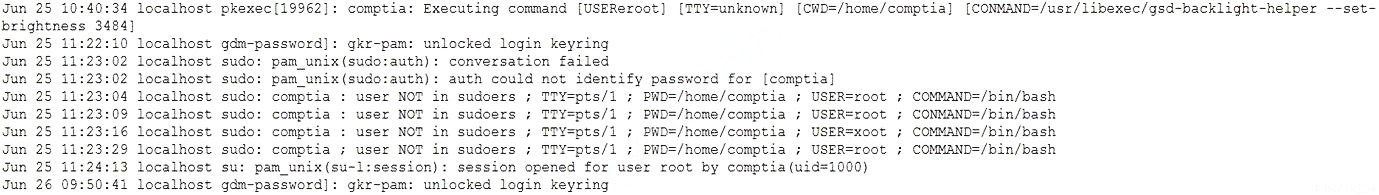
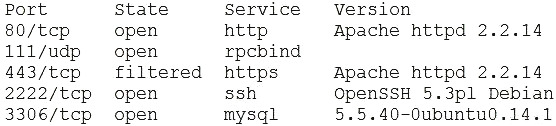
A manufacturing company uses a third-party service provider for Tier 1 security support. One of the requirements is that the provider must only source talent from its own country due to geopolitical and national security interests. Which of the following can the manufacturing company implement to ensure the third-party service provider meets this requirement?
A. Implement a secure supply chain program with governance.
B. Implement blacklisting for IP addresses from outside the country
C. Implement strong authentication controls for all contractors.
D. Implement user behavior analytics for key staff members.
A. Implement a secure supply chain program with governance.
B. Implement blacklisting for IP addresses from outside the country
C. Implement strong authentication controls for all contractors.
D. Implement user behavior analytics for key staff members.