During a review of the vulnerability scan results on a server, an information security analyst notices the following:
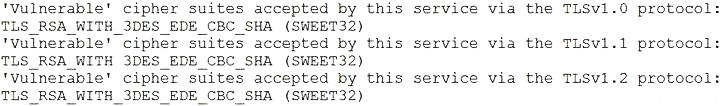
The MOST appropriate action for the analyst to recommend to developers is to change the web server so:
A. it only accepts TLSv1 .2.
B. it only accepts cipher suites using AES and SHA.
C. it no longer accepts the vulnerable cipher suites.
D. SSL/TLS is offloaded to a WAF and load balancer.

The MOST appropriate action for the analyst to recommend to developers is to change the web server so:
A. it only accepts TLSv1 .2.
B. it only accepts cipher suites using AES and SHA.
C. it no longer accepts the vulnerable cipher suites.
D. SSL/TLS is offloaded to a WAF and load balancer.