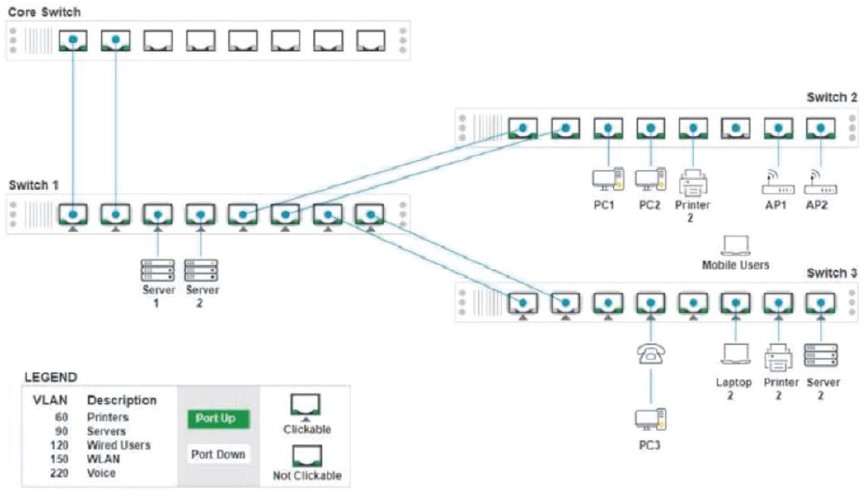
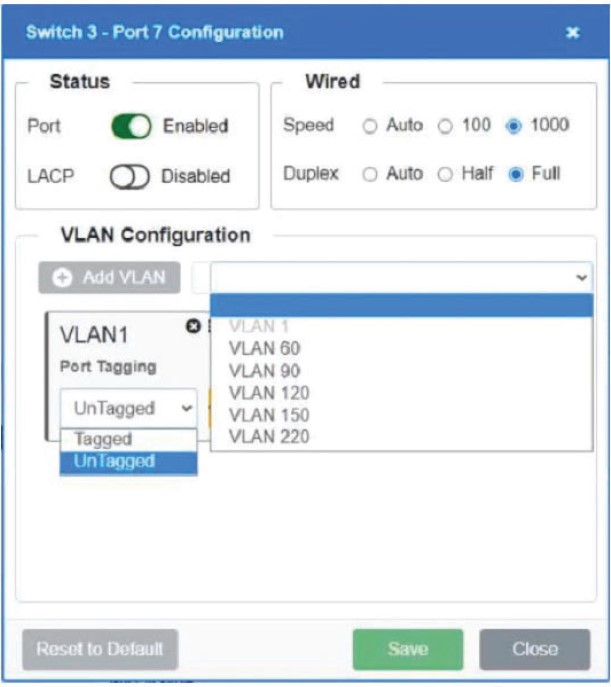
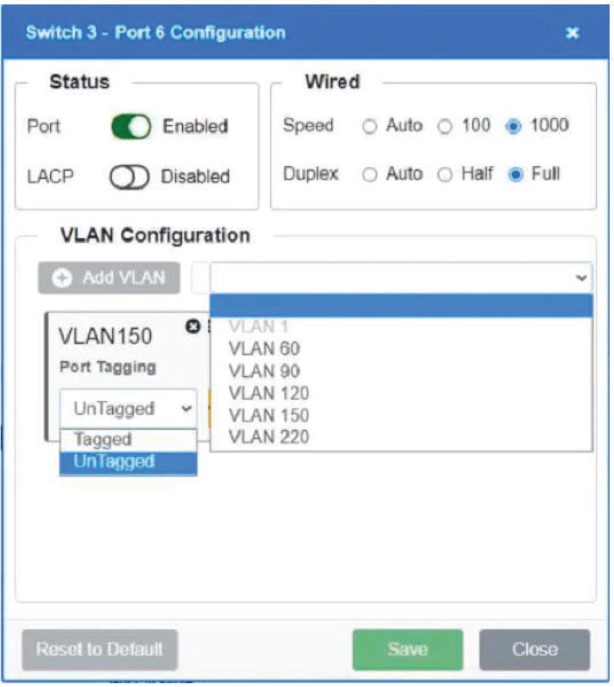
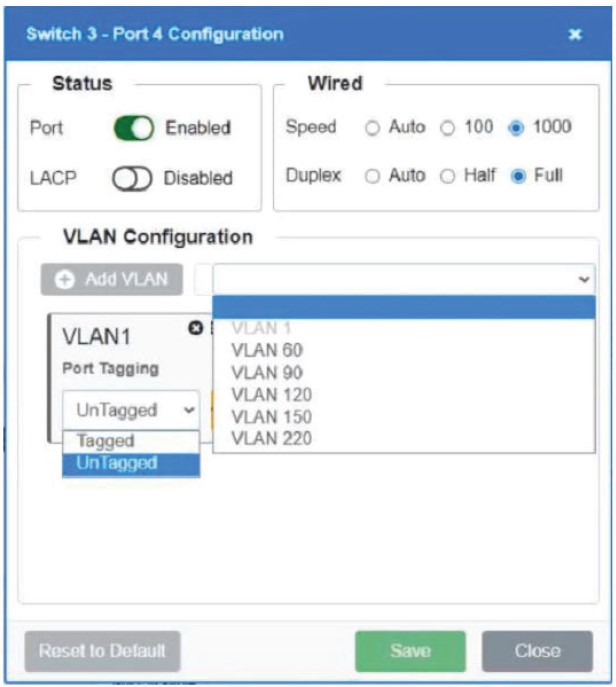
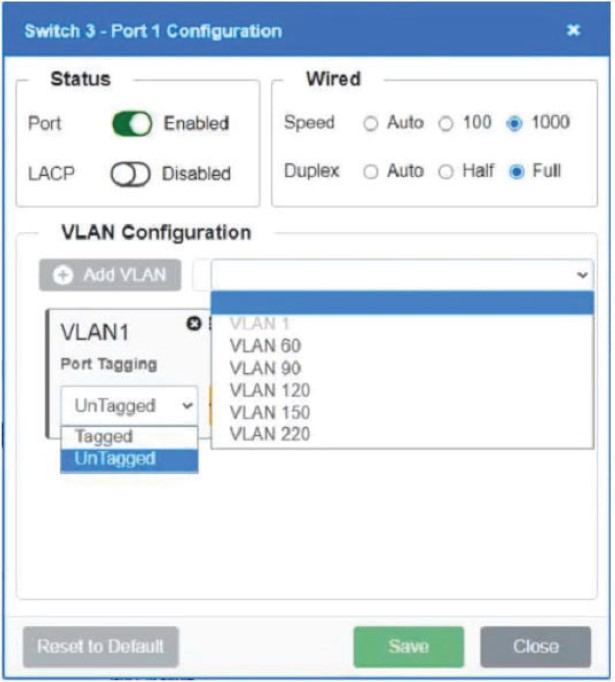
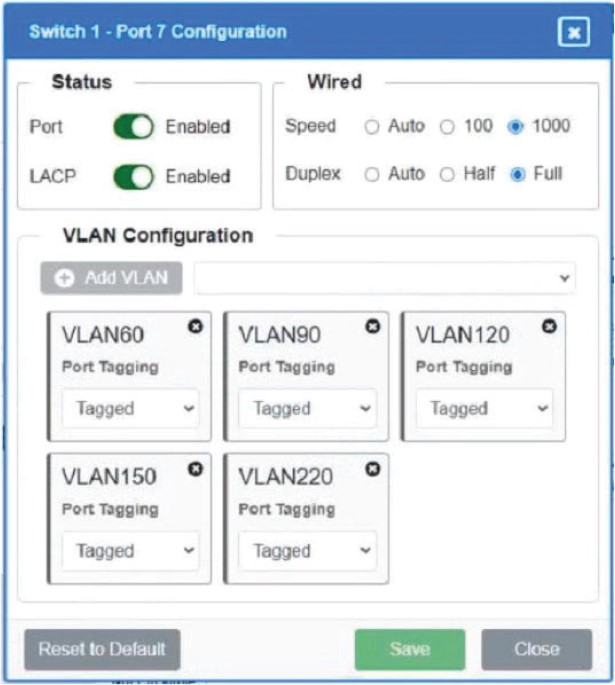
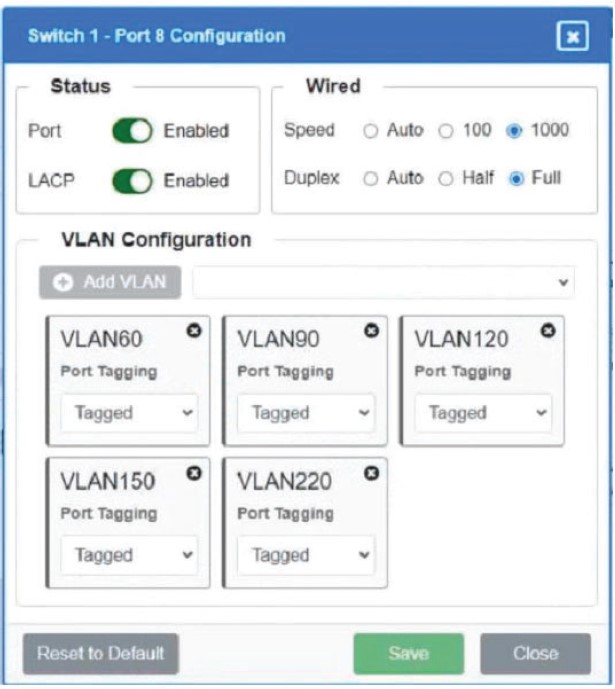
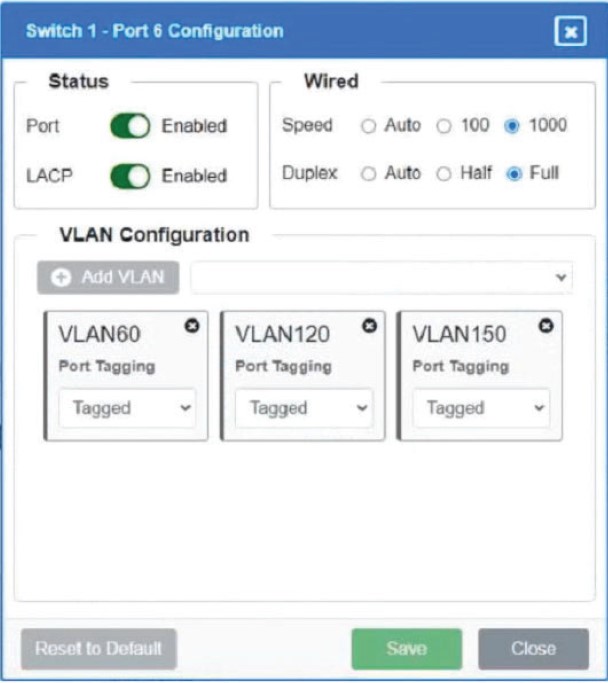
Which of the following is MOST appropriate for enforcing bandwidth limits when the performance of an
application is not affected by the use of buffering but is heavily impacted by packet drops?
A. Traffic shaping
B. Traffic policing
C. Traffic marking
D. Traffic classification
application is not affected by the use of buffering but is heavily impacted by packet drops?
A. Traffic shaping
B. Traffic policing
C. Traffic marking
D. Traffic classification