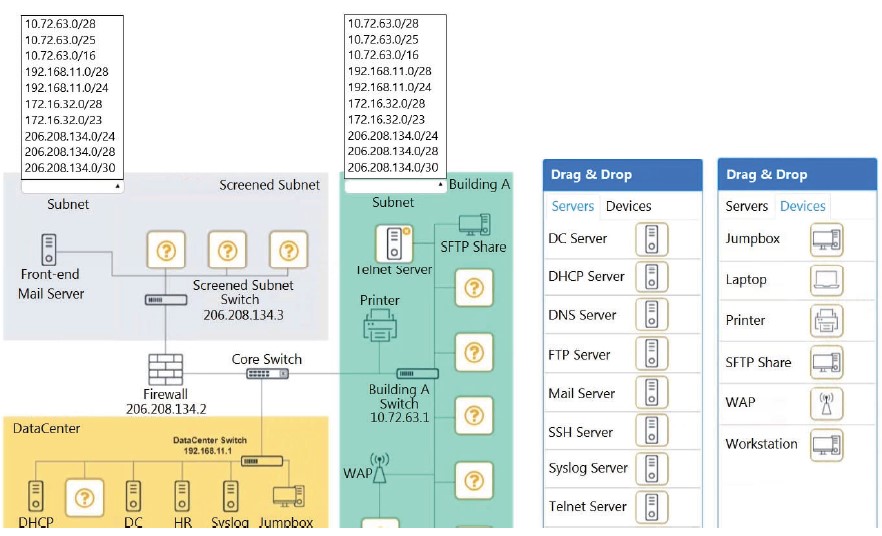
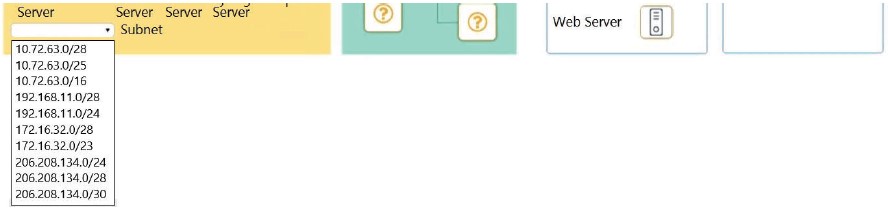
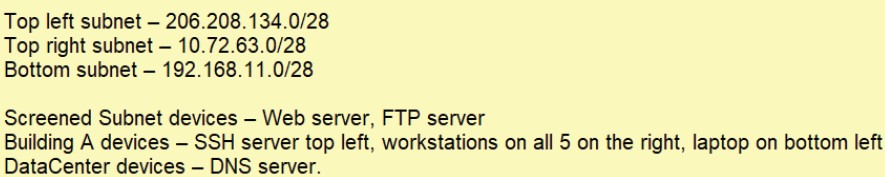
An attacker is attempting to find the password to a network by inputting common words and phrases in plaintext
to the password prompt. Which of the following attack types BEST describes this action?
A. Pass-the-hash attack
B. Rainbow table attack
C. Brute-force attack
D. Dictionary attack
to the password prompt. Which of the following attack types BEST describes this action?
A. Pass-the-hash attack
B. Rainbow table attack
C. Brute-force attack
D. Dictionary attack