SIMULATION
You are a penetration tester running port scans on a server.
INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
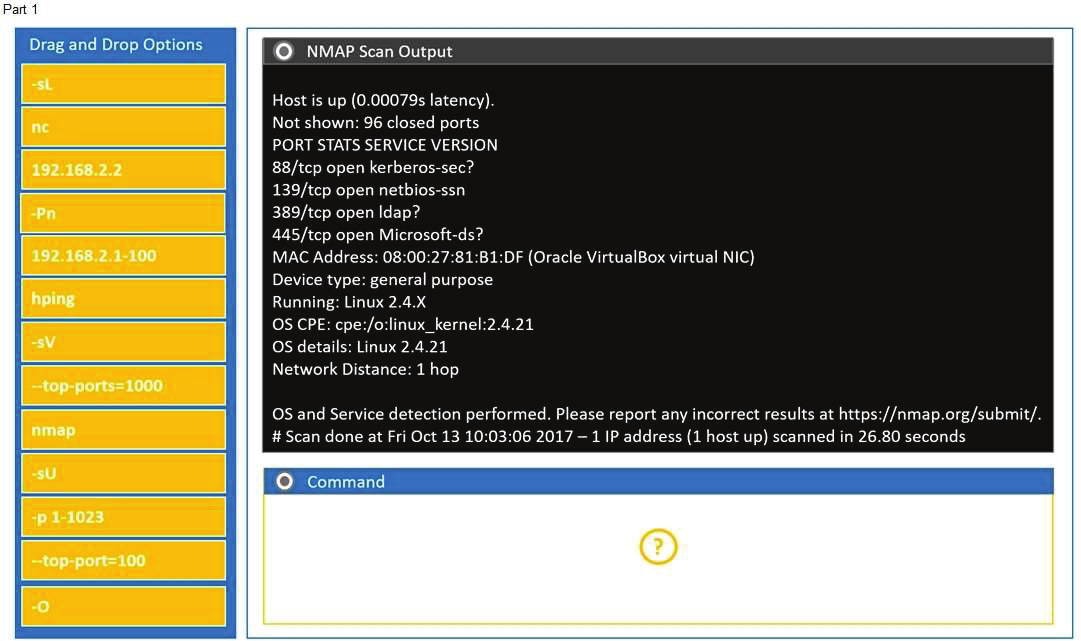
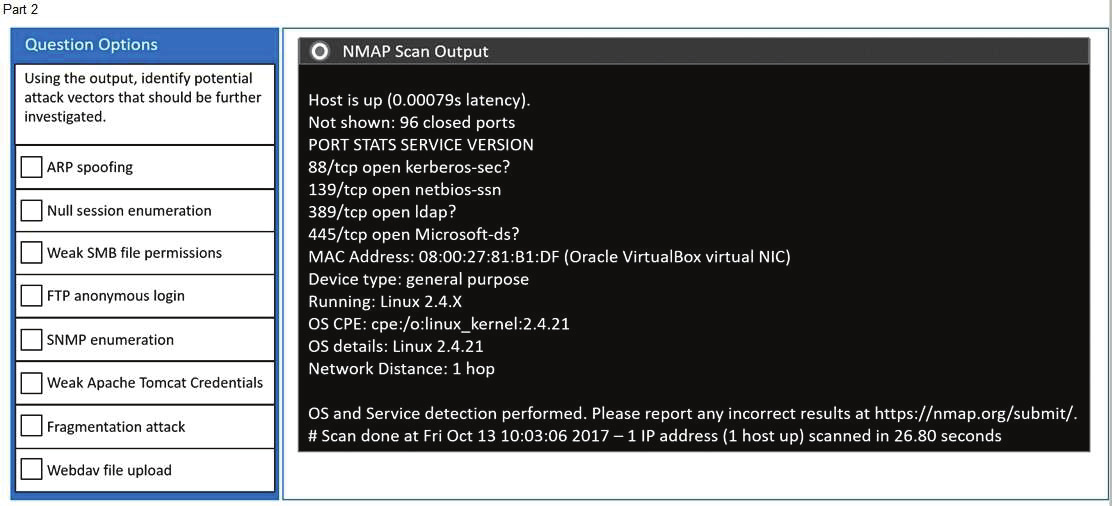
You are a penetration tester running port scans on a server.
INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.

