A penetration tester downloaded a Java application file from a compromised web server and identifies how to invoke it by looking at the following log:
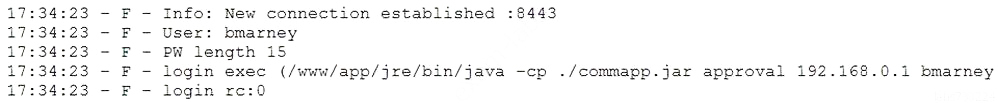
Which of the following is the order of steps the penetration tester needs to follow to validate whether the Java application uses encryption over sockets?
A. Run an application vulnerability scan and then identify the TCP ports used by the application.
B. Run the application attached to a debugger and then review the application's log.
C. Disassemble the binary code and then identify the break points.
D. Start a packet capture with Wireshark and then run the application.

Which of the following is the order of steps the penetration tester needs to follow to validate whether the Java application uses encryption over sockets?
A. Run an application vulnerability scan and then identify the TCP ports used by the application.
B. Run the application attached to a debugger and then review the application's log.
C. Disassemble the binary code and then identify the break points.
D. Start a packet capture with Wireshark and then run the application.