A penetration tester downloaded the following Perl script that can be used to identify vulnerabilities in network switches. However, the script is not working properly.
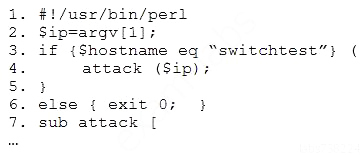
Which of the following changes should the tester apply to make the script work as intended?
A. Change line 2 to $ip= "10.192.168.254";
B. Remove lines 3, 5, and 6.
C. Remove line 6.
D. Move all the lines below line 7 to the top of the script.

Which of the following changes should the tester apply to make the script work as intended?
A. Change line 2 to $ip= "10.192.168.254";
B. Remove lines 3, 5, and 6.
C. Remove line 6.
D. Move all the lines below line 7 to the top of the script.