A penetration tester captured the following traffic during a web-application test:
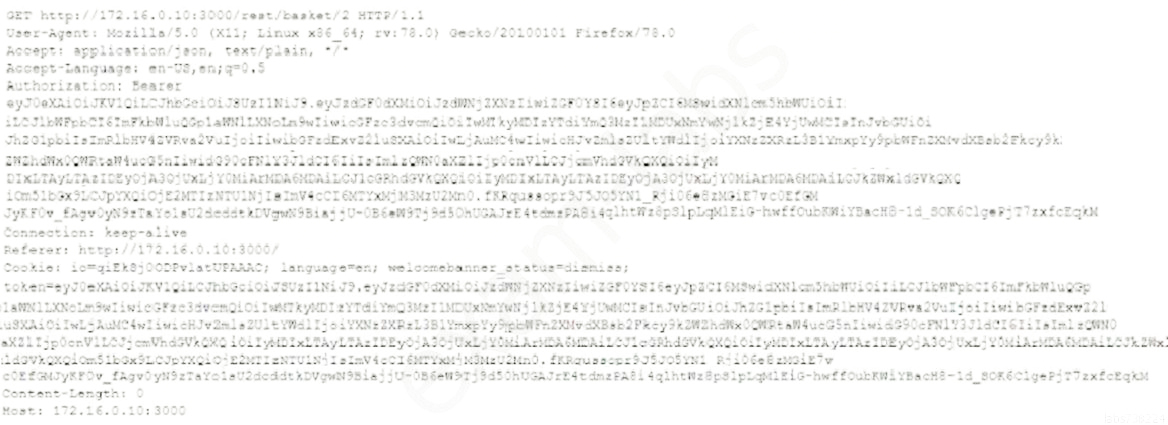
Which of the following methods should the tester use to visualize the authorization information being transmitted?
A. Decode the authorization header using UTF-8.
B. Decrypt the authorization header using bcrypt.
C. Decode the authorization header using Base64.
D. Decrypt the authorization header using AES.

Which of the following methods should the tester use to visualize the authorization information being transmitted?
A. Decode the authorization header using UTF-8.
B. Decrypt the authorization header using bcrypt.
C. Decode the authorization header using Base64.
D. Decrypt the authorization header using AES.