An Nmap scan of a network switch reveals the following:
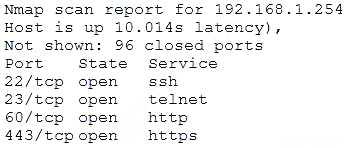
Which of the following technical controls will most likely be the FIRST recommendation for this device?
A. Encrypted passwords
B. System-hardening techniques
C. Multifactor authentication
D. Network segmentation

Which of the following technical controls will most likely be the FIRST recommendation for this device?
A. Encrypted passwords
B. System-hardening techniques
C. Multifactor authentication
D. Network segmentation