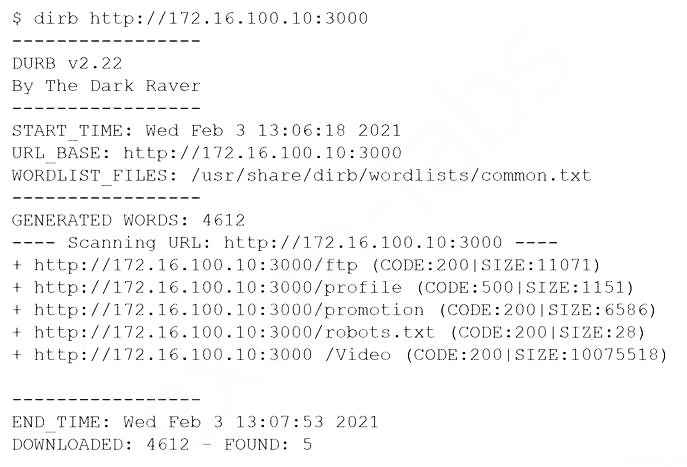
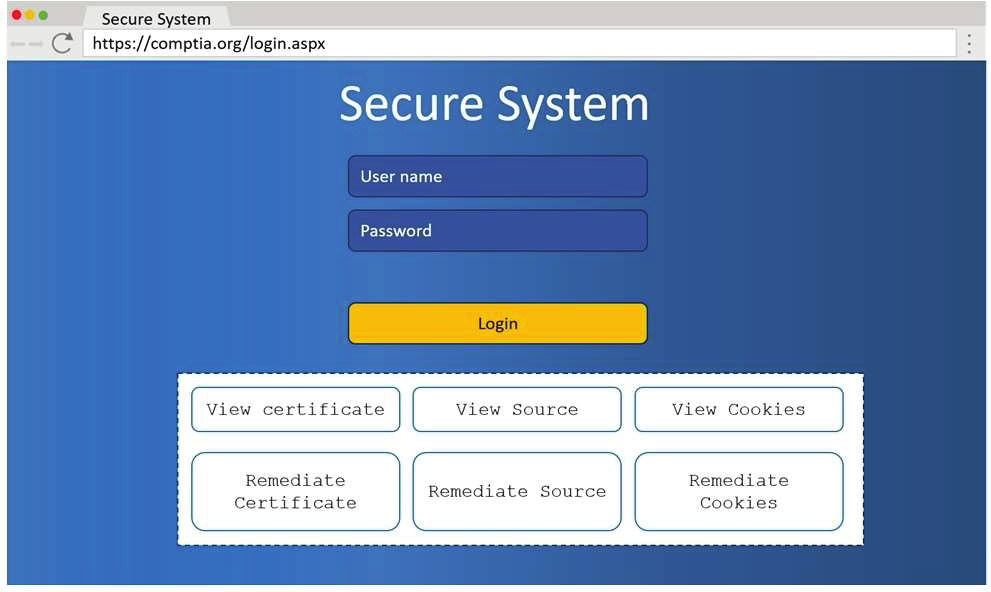
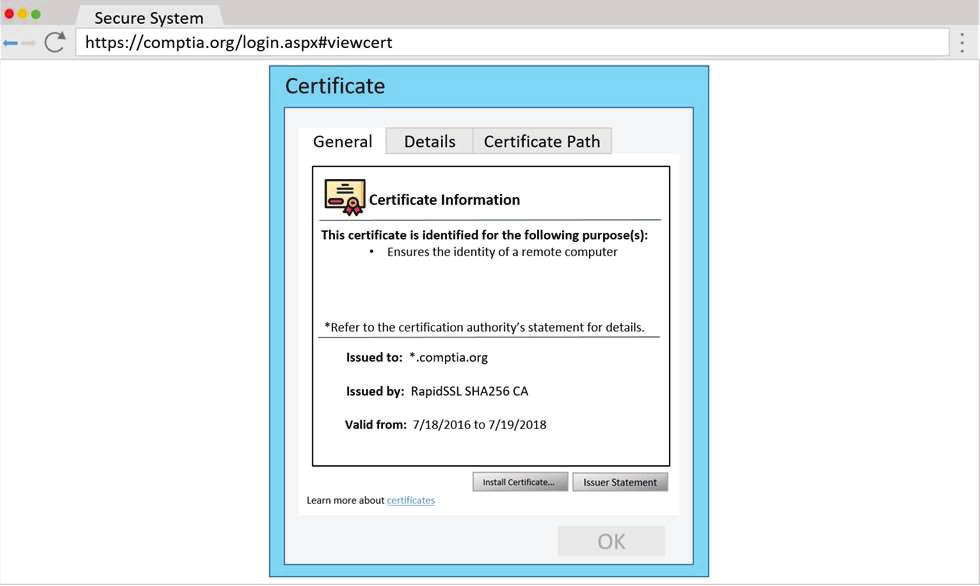
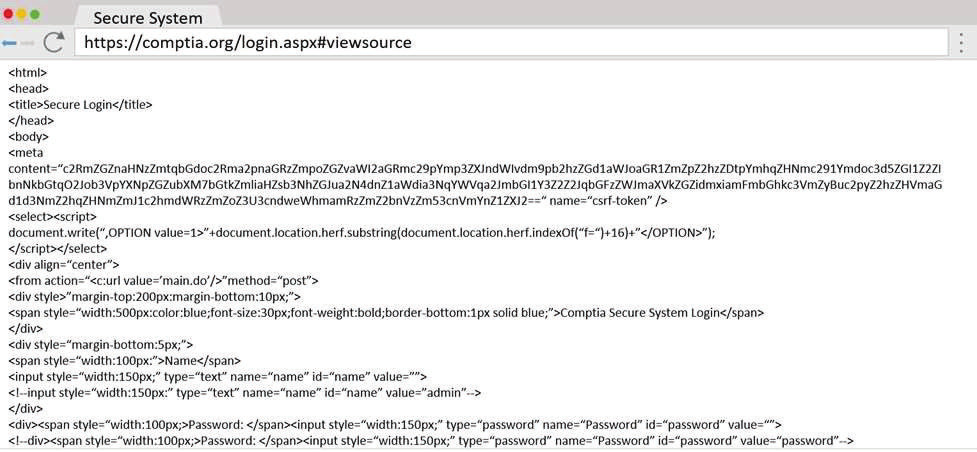
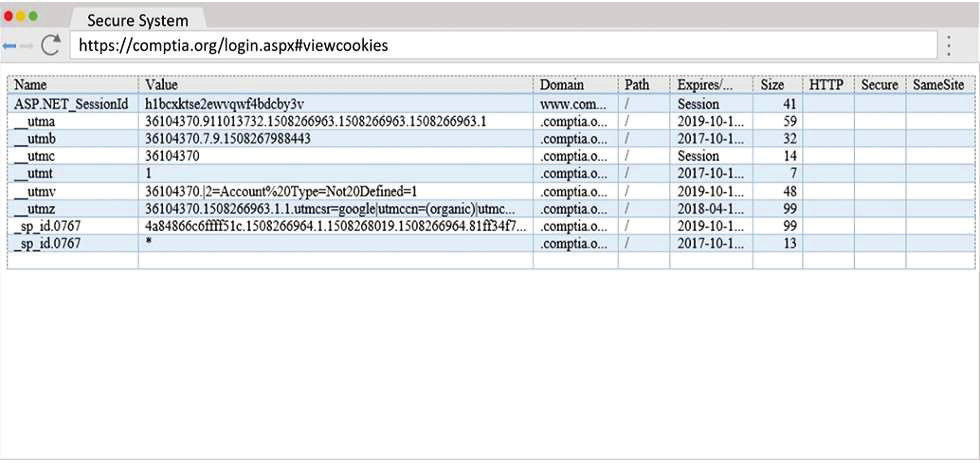
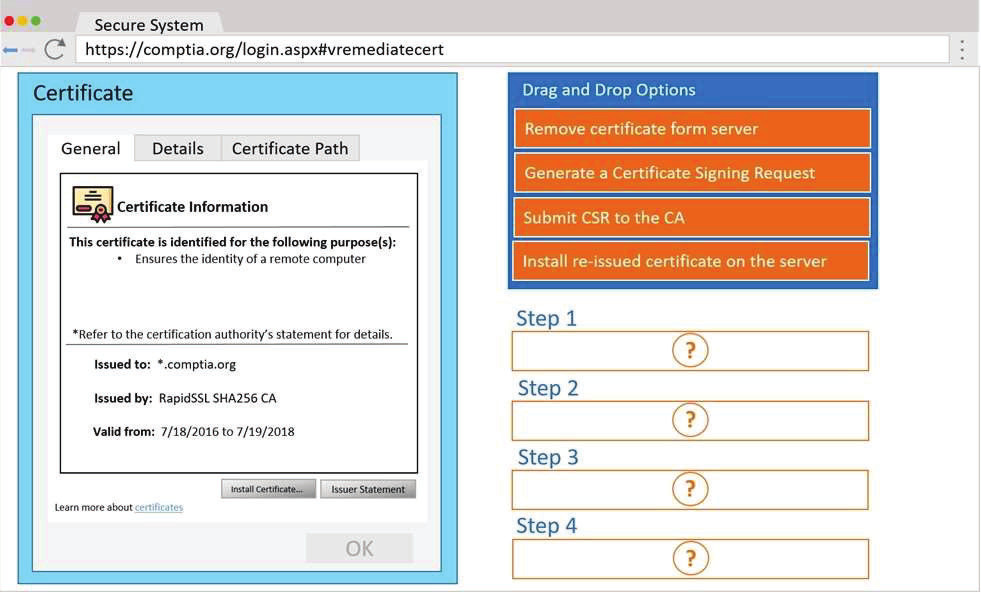
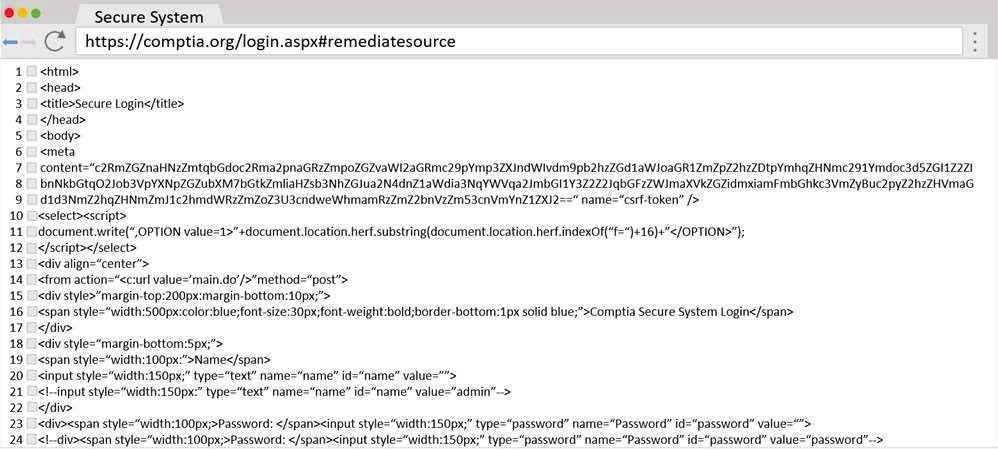
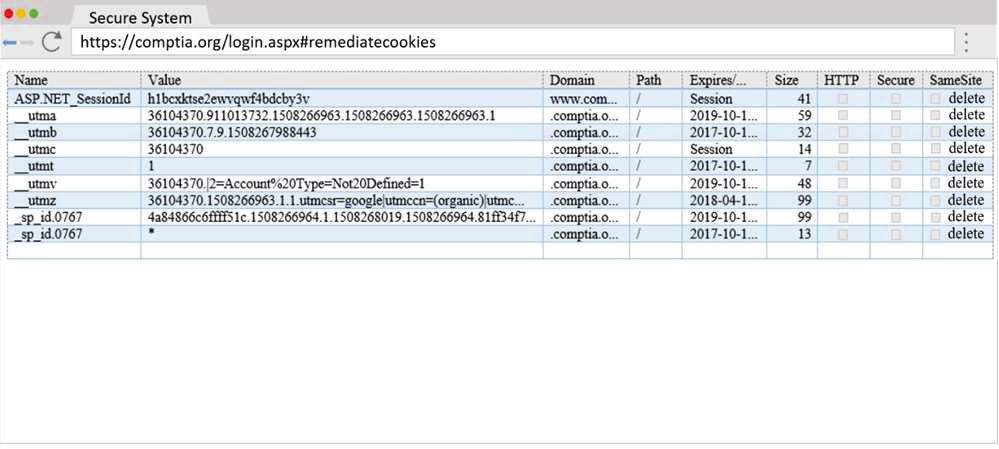
A penetration tester wants to identify CVEs that can be leveraged to gain execution on a Linux server that has an SSHD running.
Which of the following would BEST support this task?
A. Run nmap with the -O, -p22, and -sC options set against the target.
B. Run nmap with the -sV and -p22 options set against the target.
C. Run nmap with the –script vulners option set against the target.
D. Run nmap with the -sA option set against the target.
Which of the following would BEST support this task?
A. Run nmap with the -O, -p22, and -sC options set against the target.
B. Run nmap with the -sV and -p22 options set against the target.
C. Run nmap with the –script vulners option set against the target.
D. Run nmap with the -sA option set against the target.