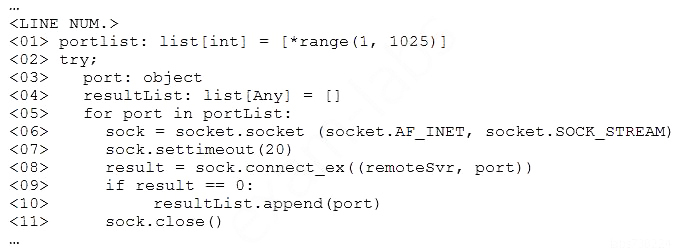
A penetration tester is conducting an authorized, physical penetration test to attempt to enter a client's building during non-business hours. Which of the following are MOST important for the penetration tester to have during the test? (Choose two.)
A. A handheld RF spectrum analyzer
B. A mask and personal protective equipment
C. Caution tape for marking off insecure areas
D. A dedicated point of contact at the client
E. The paperwork documenting the engagement
F. Knowledge of the building's normal business hours
A. A handheld RF spectrum analyzer
B. A mask and personal protective equipment
C. Caution tape for marking off insecure areas
D. A dedicated point of contact at the client
E. The paperwork documenting the engagement
F. Knowledge of the building's normal business hours