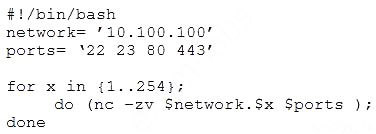
An Nmap network scan has found five open ports with identified services. Which of the following tools should a penetration tester use NEXT to determine if any vulnerabilities with associated exploits exist on the open ports?
A. OpenVAS
B. Drozer
C. Burp Suite
D. OWASP ZAP
A. OpenVAS
B. Drozer
C. Burp Suite
D. OWASP ZAP