During an engagement, a penetration tester found the following list of strings inside a file:
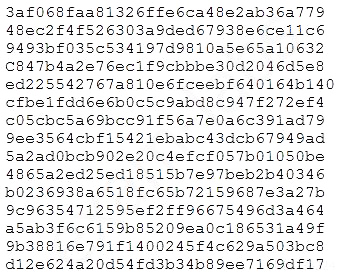
Which of the following is the BEST technique to determine the known plaintext of the strings?
A. Dictionary attack
B. Rainbow table attack
C. Brute-force attack
D. Credential-stuffing attack

Which of the following is the BEST technique to determine the known plaintext of the strings?
A. Dictionary attack
B. Rainbow table attack
C. Brute-force attack
D. Credential-stuffing attack