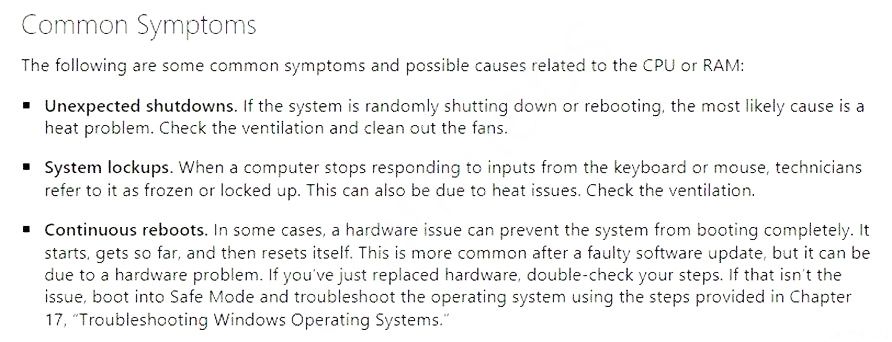
A technician has received multiple reports of issues with a server. The server occasionally has a BSOD, powers off unexpectedly, and has fans that run continuously. Which of the following BEST represents what the technician should investigate during troubleshooting?
A. Firmware incompatibility
B. CPU overheating
C. LED indicators
D. ESD issues
A. Firmware incompatibility
B. CPU overheating
C. LED indicators
D. ESD issues