Which one of the following Google advanced search operators allows an attacker to restrict the results to those websites in the given domain?
A. [cache:]
B. [site:]
C. [inurl:]
D. [link:]
A. [cache:]
B. [site:]
C. [inurl:]
D. [link:]
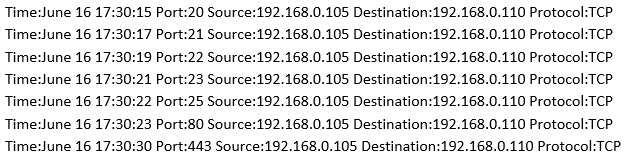
What type of activity has been logged?
A. Teardrop attack targeting 192.168.0.110
B. Denial of service attack targeting 192.168.0.105
C. Port scan targeting 192.168.0.110
D. Port scan targeting 192.168.0.105