Which tool allows analysts and pen testers to examine links between data using graphs and link analysis?
A. Metasploit
B. Cain & Abel
C. Maltego
D. Wireshark
A. Metasploit
B. Cain & Abel
C. Maltego
D. Wireshark
What kind of Web application vulnerability likely exists in their software?
A. Cross-site scripting vulnerability
B. Web site defacement vulnerability
C. SQL injection vulnerability
D. Cross-site Request Forgery vulnerability
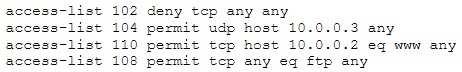
A. The ACL 104 needs to be first because is UDP
B. The ACL 110 needs to be changed to port 80
C. The ACL for FTP must be before the ACL 110
D. The first ACL is denying all TCP traffic and the other ACLs are being ignored by the router
What is the best way to evade the NIDS?
A. Out of band signaling
B. Protocol Isolation
C. Encryption
D. Alternate Data Streams