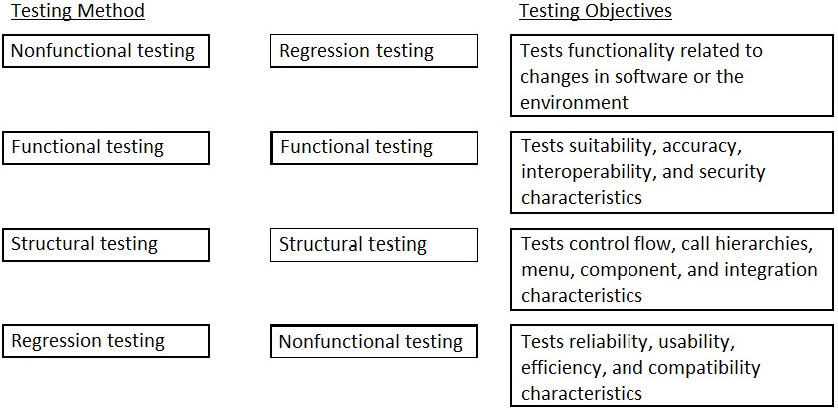
DRAG DROP Match the following generic software testing methods with their major focus and objective.
Drag each testing method next to its corresponding set of testing objectives.
Select and Place:
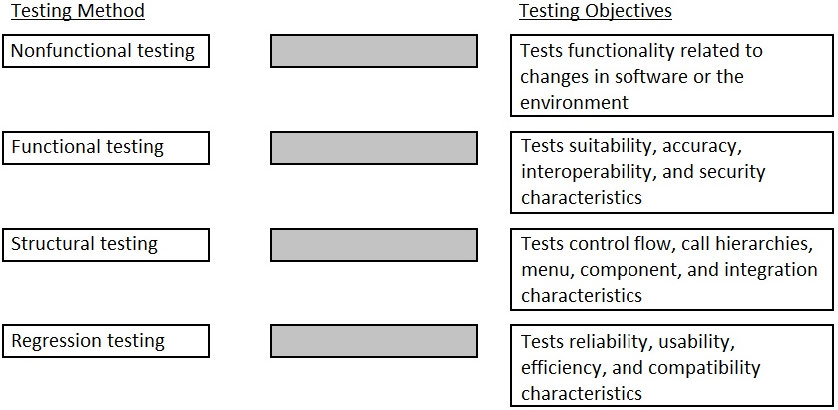
Drag each testing method next to its corresponding set of testing objectives.
Select and Place: