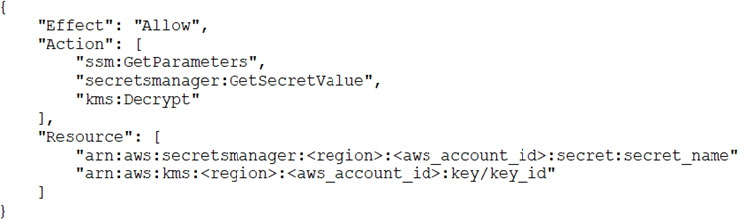
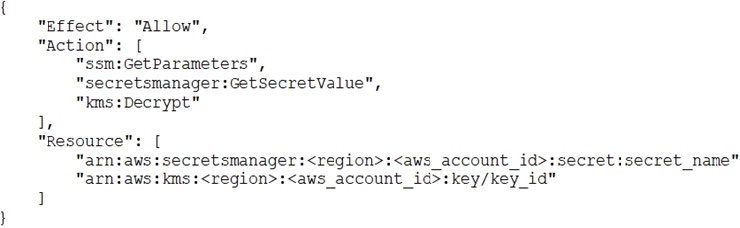
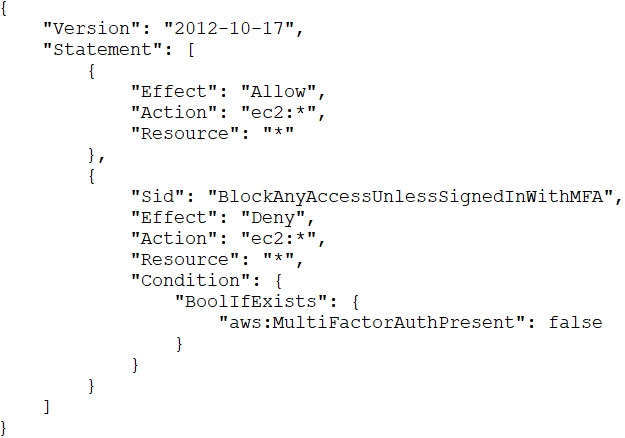
A security engineer is responsible for providing secure access to AWS resources for thousands of developers in a company’s corporate identity provider (IdP). The developers access a set of AWS services from their corporate premises using IAM credentials. Due to the volume of requests for provisioning new IAM users, it is taking a long time to grant access permissions. The security engineer receives reports that developers are sharing their IAM credentials with others to avoid provisioning delays. This causes concern about overall security for the security engineer.
Which actions will meet the program requirements that address security?
A. Create an Amazon CloudWatch alarm for AWS CloudTrail events. Create a metric filter to send a notification when the same set of IAM credentials is used by multiple developers.
B. Create a federation between AWS and the existing corporate IdP. Leverage IAM roles to provide federated access to AWS resources.
C. Create a VPN tunnel between the corporate premises and the VPC. Allow permissions to all AWS services only if it originates from corporate premises.
D. Create multiple IAM roles for each IAM user. Ensure that users who use the same IAM credentials cannot assume the same IAM role at the same time.
Which actions will meet the program requirements that address security?
A. Create an Amazon CloudWatch alarm for AWS CloudTrail events. Create a metric filter to send a notification when the same set of IAM credentials is used by multiple developers.
B. Create a federation between AWS and the existing corporate IdP. Leverage IAM roles to provide federated access to AWS resources.
C. Create a VPN tunnel between the corporate premises and the VPC. Allow permissions to all AWS services only if it originates from corporate premises.
D. Create multiple IAM roles for each IAM user. Ensure that users who use the same IAM credentials cannot assume the same IAM role at the same time.