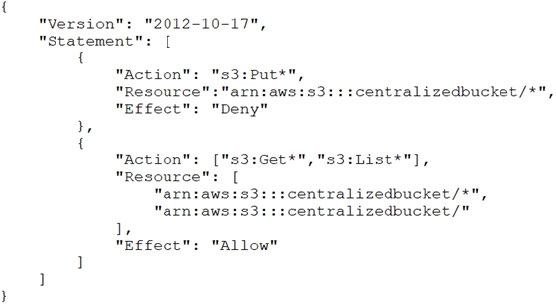
How should this be accomplished?
A. Use SCPs.
B. Add a permissions boundary to deny access to Amazon S3 and attach it to all roles.
C. Use an S3 bucket policy.
D. Create a VPC endpoint for Amazon S3 and deny statements for access to Amazon S3.
Which approach meets these requirements?
A. Modify the application to use the AWS SDK. Write the application logs to an Amazon S3 bucket.
B. Install the unified Amazon CloudWatch agent on the instances. Configure the agent to collect the application log files on the EC2 file system and send them to Amazon CloudWatch Logs.
C. Install AWS Systems Manager Agent on the instances. Configure an automation document to copy the application log files to AWS DeepLens.
D. Install Amazon Kinesis Agent on the instances. Stream the application log files to Amazon Kinesis Data Firehose and set the destination to Amazon Elasticsearch Service.