The application must:
- Include migration to a different AWS Region in the application disaster recovery plan.
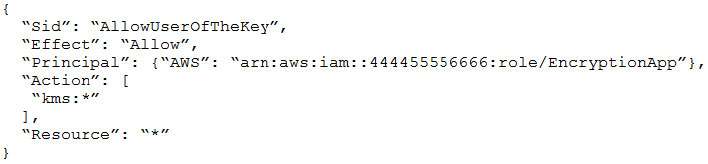
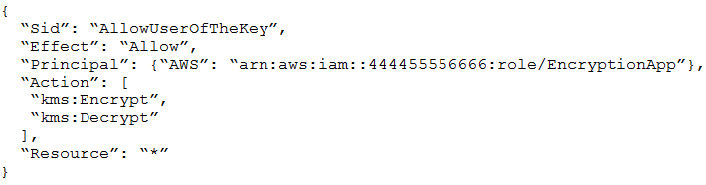
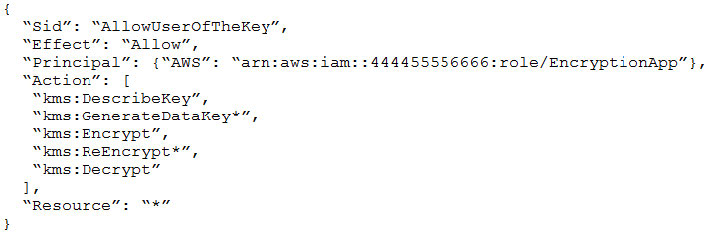
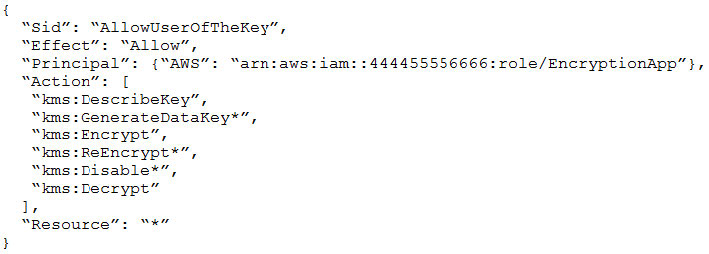
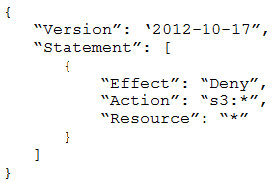
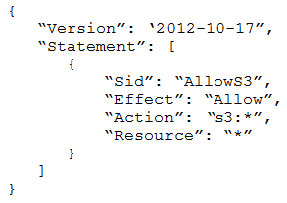
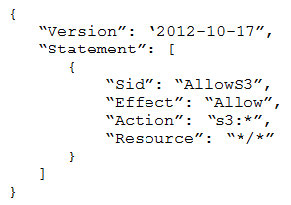
- Provide a full audit trail of encryption key administration events.
- Allow only company administrators to administer keys.
- Protect data at rest using application layer encryption.
A Security Engineer is evaluating options for encryption key management.
Why should the Security Engineer choose AWS CloudHSM over AWS KMS for encryption key management in this situation?
A. The key administration event logging generated by CloudHSM is significantly more extensive than AWS KMS.
B. CloudHSM ensures that only company support staff can administer encryption keys, whereas AWS KMS allows AWS staff to administer keys.
C. The ciphertext produced by CloudHSM provides more robust protection against brute force decryption attacks than the ciphertext produced by AWS KMS.
D. CloudHSM provides the ability to copy keys to a different Region, whereas AWS KMS does not.