An AWS account administrator created an IAM group and applied the following managed policy to require that each individual user authenticate using multi-factor authentication:
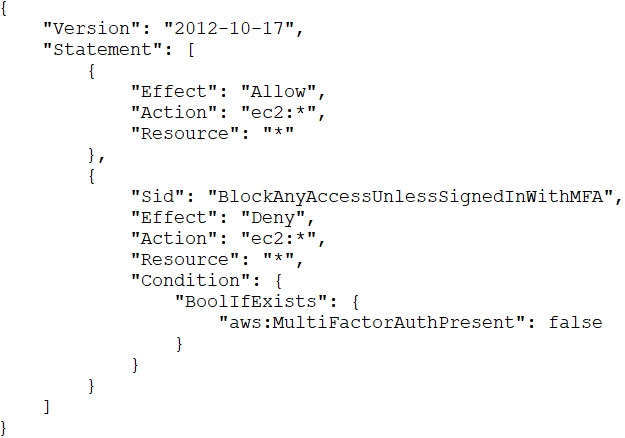
After implementing the policy, the administrator receives reports that users are unable to perform Amazon EC2 commands using the AWS CLI.
What should the administrator do to resolve this problem while still enforcing multi-factor authentication?
A. Change the value of aws:MultiFactorAuthPresent to true.
B. Instruct users to run the aws sts get-session-token CLI command and pass the multi-factor authentication –serial-number and –token-code parameters. Use these resulting values to make API/CLI calls.
C. Implement federated API/CLI access using SAML 2.0, then configure the identity provider to enforce multi-factor authentication.
D. Create a role and enforce multi-factor authentication in the role trust policy. Instruct users to run the sts assume-role CLI command and pass –serial-number and –token-code parameters. Store the resulting values in environment variables. Add sts:AssumeRole to NotAction in the policy.

After implementing the policy, the administrator receives reports that users are unable to perform Amazon EC2 commands using the AWS CLI.
What should the administrator do to resolve this problem while still enforcing multi-factor authentication?
A. Change the value of aws:MultiFactorAuthPresent to true.
B. Instruct users to run the aws sts get-session-token CLI command and pass the multi-factor authentication –serial-number and –token-code parameters. Use these resulting values to make API/CLI calls.
C. Implement federated API/CLI access using SAML 2.0, then configure the identity provider to enforce multi-factor authentication.
D. Create a role and enforce multi-factor authentication in the role trust policy. Instruct users to run the sts assume-role CLI command and pass –serial-number and –token-code parameters. Store the resulting values in environment variables. Add sts:AssumeRole to NotAction in the policy.