A security analyst reviews web server logs and notices the following lines:
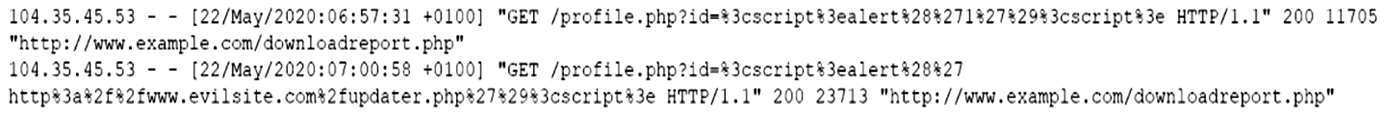
Which of the following vulnerabilities is the attacker trying to exploit?
A. Token reuse
B. SQLi
C. CSRF
D. XSS

Which of the following vulnerabilities is the attacker trying to exploit?
A. Token reuse
B. SQLi
C. CSRF
D. XSS