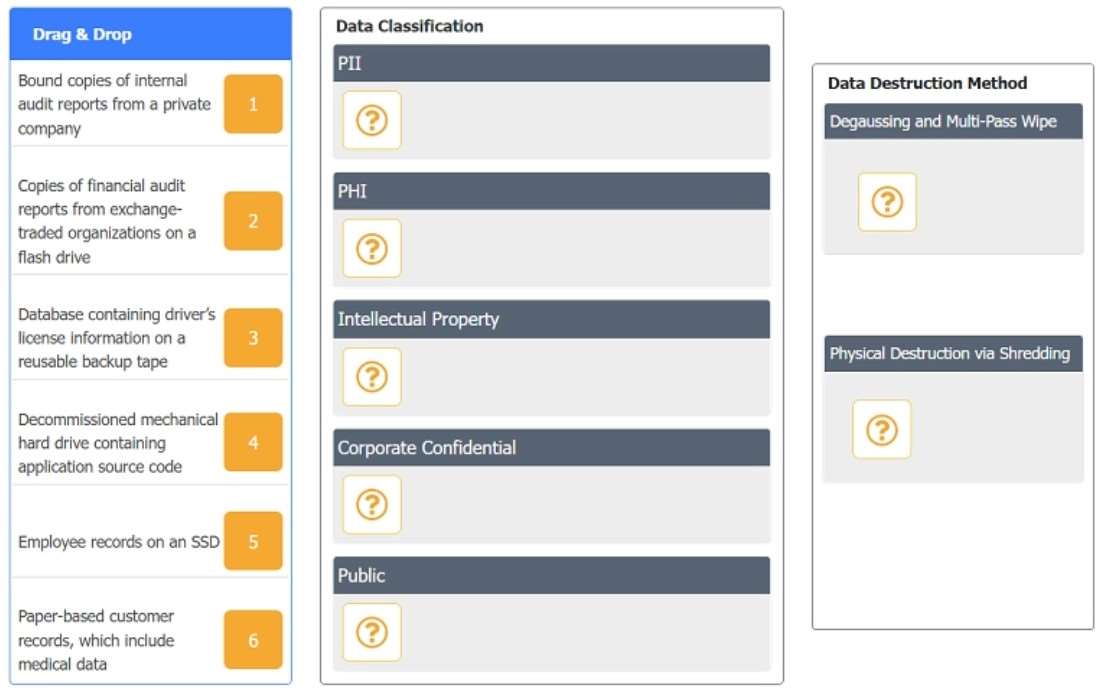
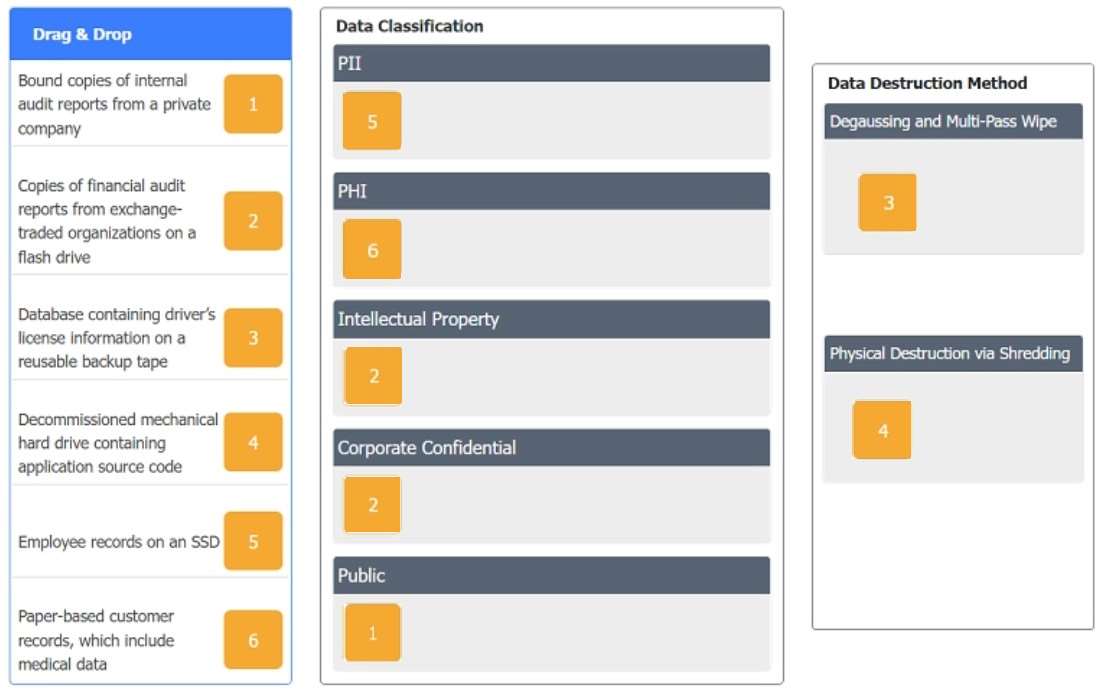
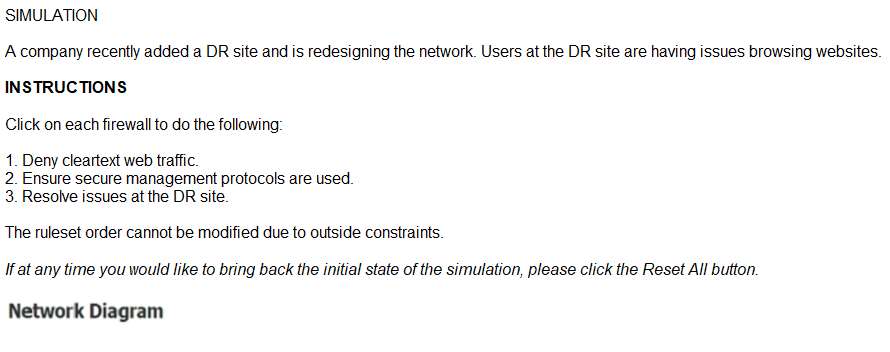
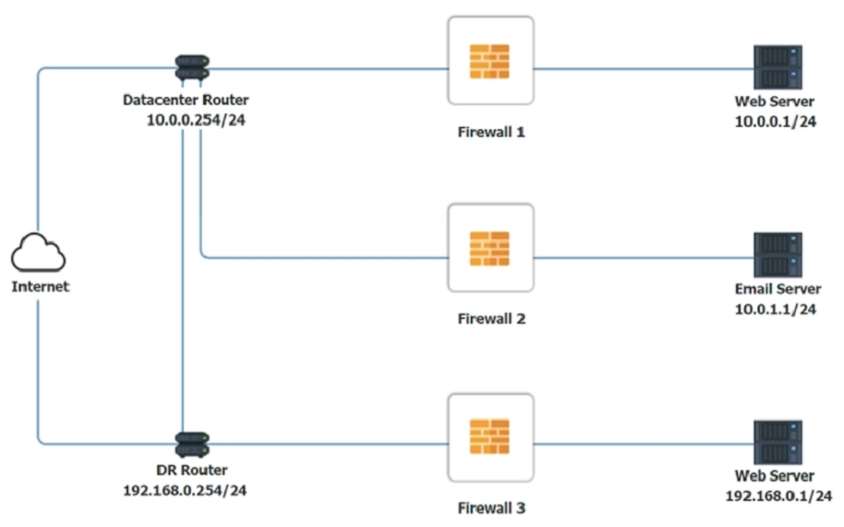
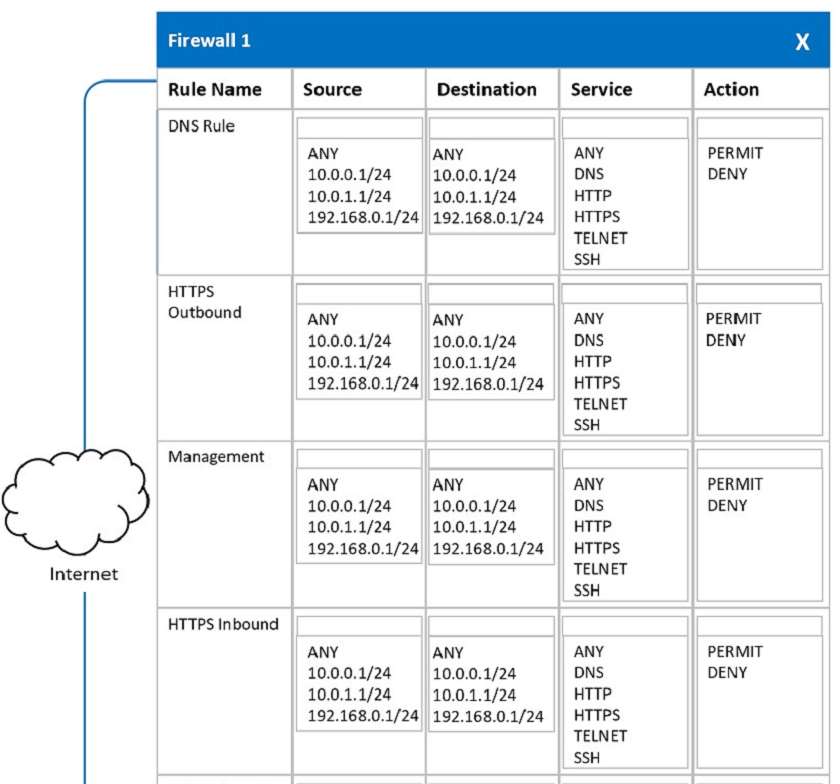
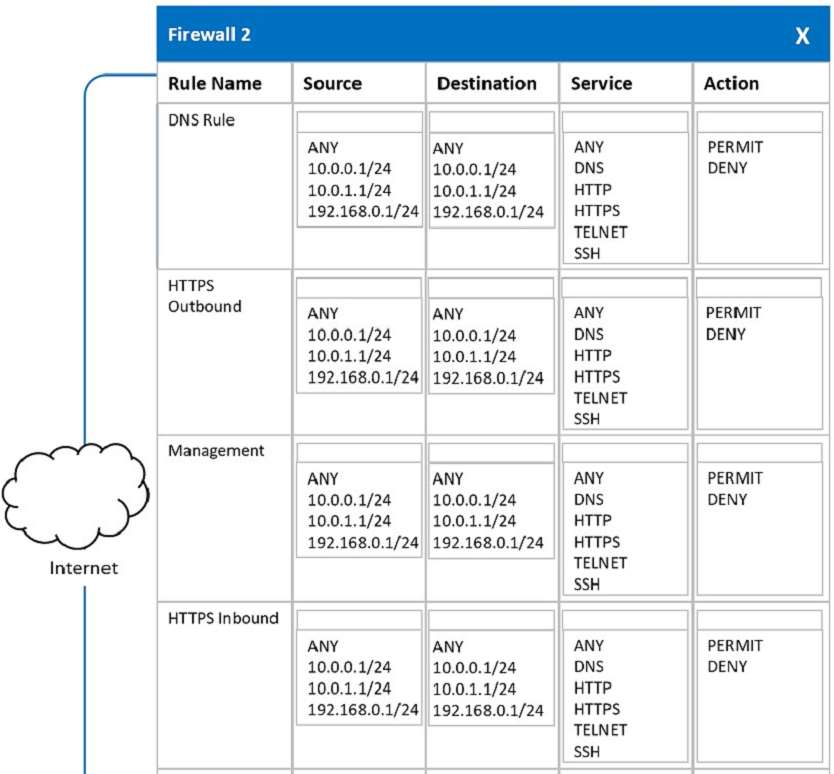
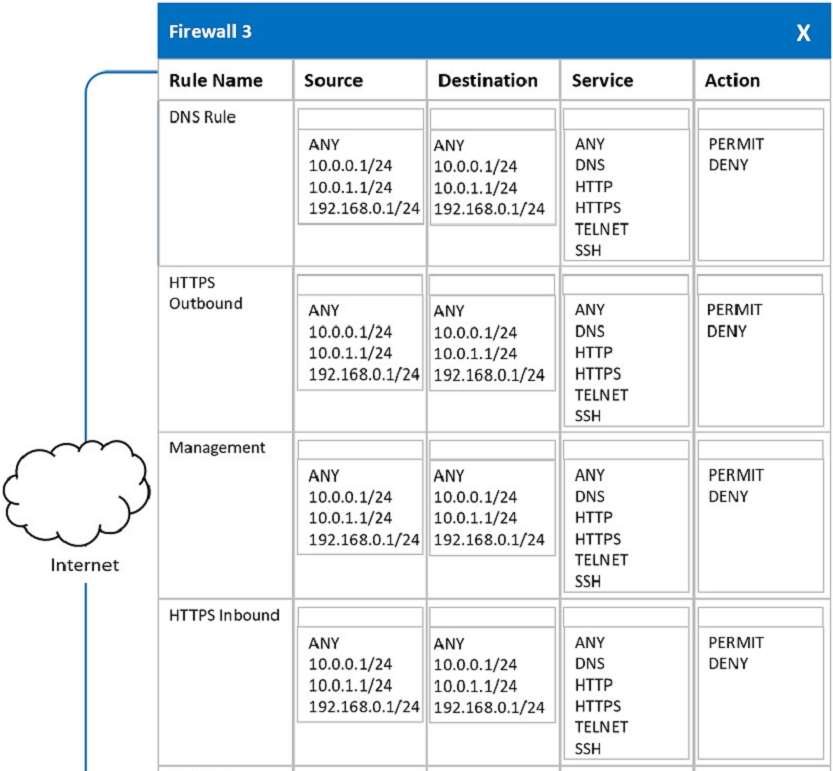
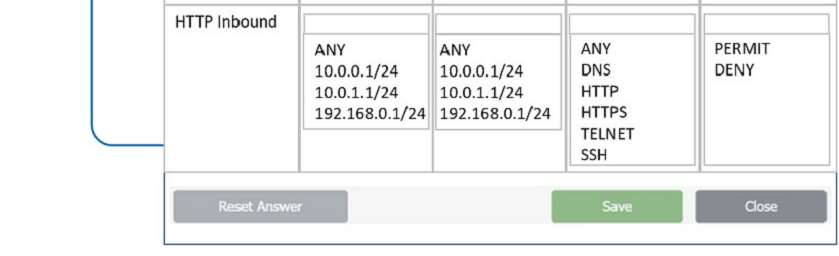
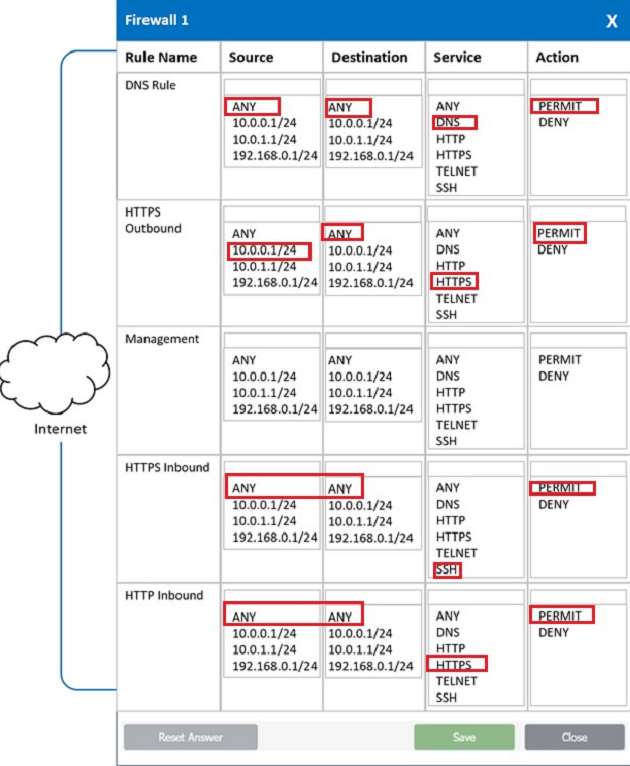
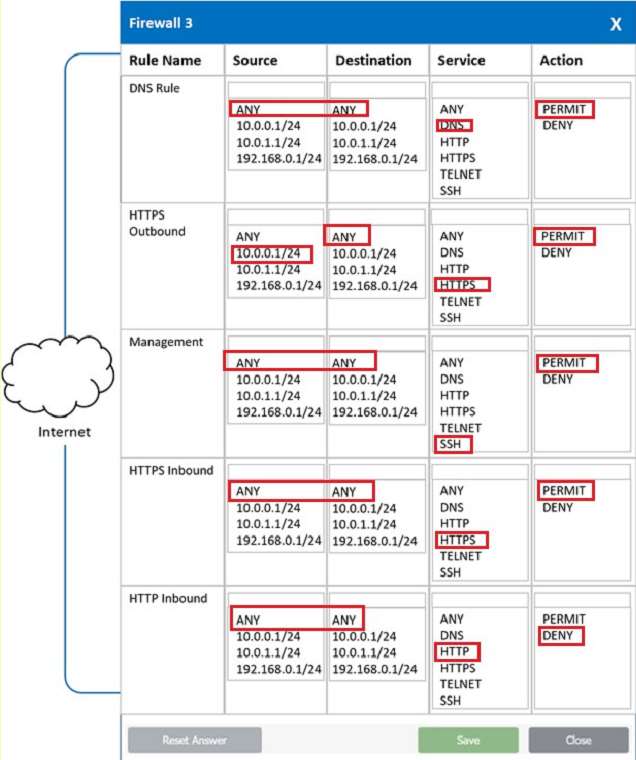
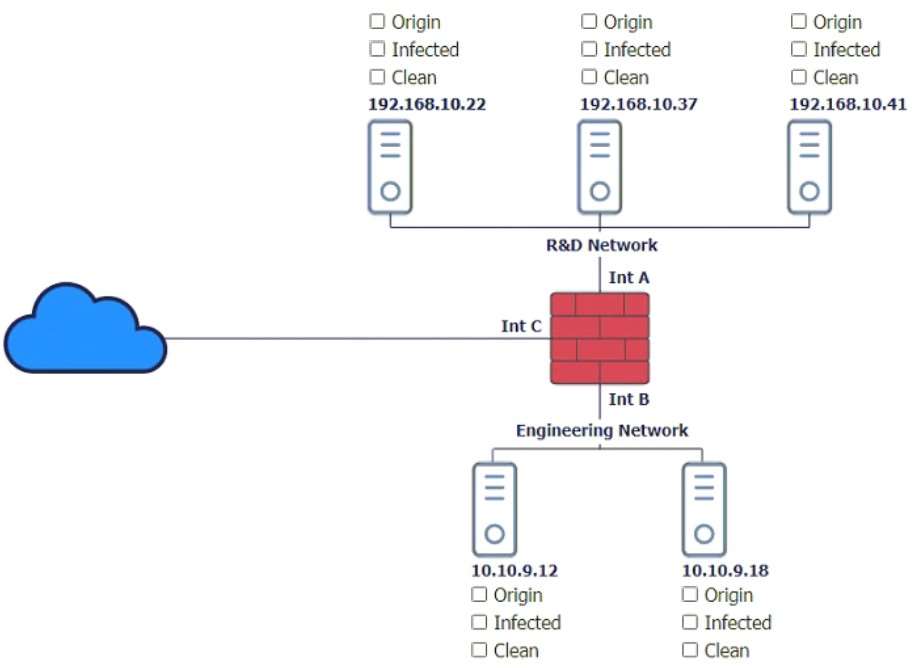
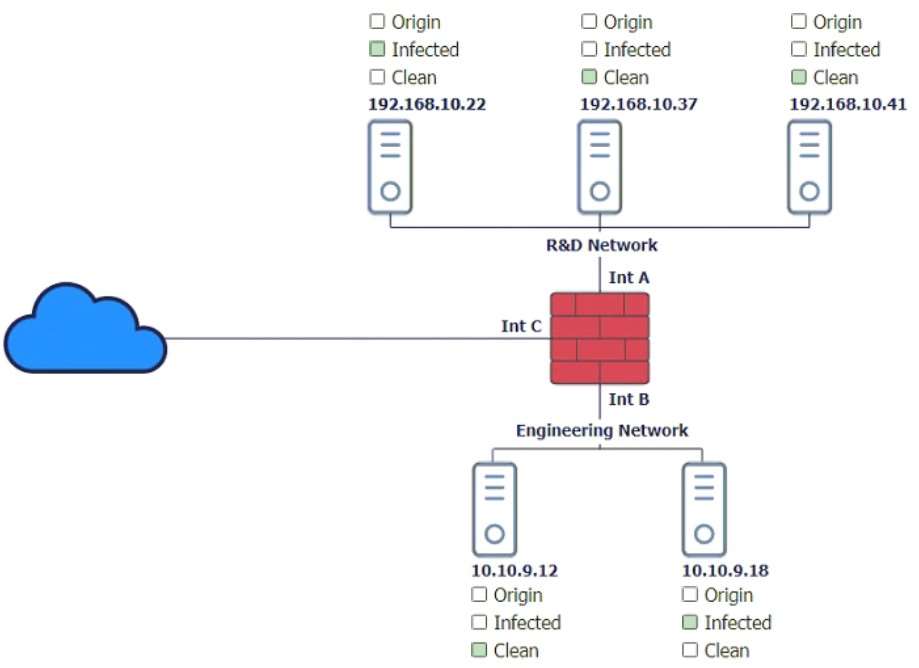
In a rush to meet an end-of-year business goal, the IT department was told to implement a new business application. The security engineer reviews the attributes of the application and decides the time needed to perform due diligence is insufficient from a cybersecurity perspective. Which of the following BEST describes the security engineer's response?
A. Risk tolerance
B. Risk acceptance
C. Risk importance
D. Risk appetite
A. Risk tolerance
B. Risk acceptance
C. Risk importance
D. Risk appetite