A security analyst reviews web server logs and notices the following lines:
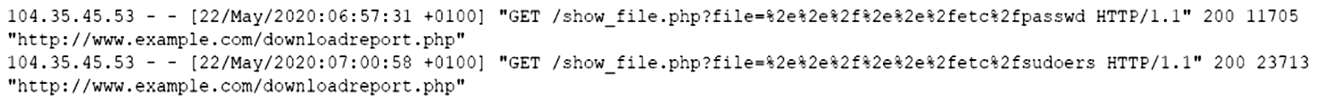
Which of the following vulnerabilities has the attacker exploited? (Choose two.)
A. Race condition
B. LFI
C. Pass the hash
D. XSS
E. RFI
F. Directory traversal

Which of the following vulnerabilities has the attacker exploited? (Choose two.)
A. Race condition
B. LFI
C. Pass the hash
D. XSS
E. RFI
F. Directory traversal