A security analyst is reviewing the following logs:
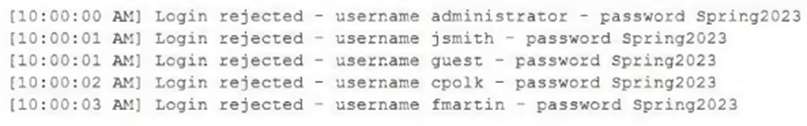
Which of the following attacks is most likely occurring?
A. Password spraying
B. Account forgery
C. Pass-the-hash
D. Brute-force