A SOC operator is analyzing a log file that contains the following entries:
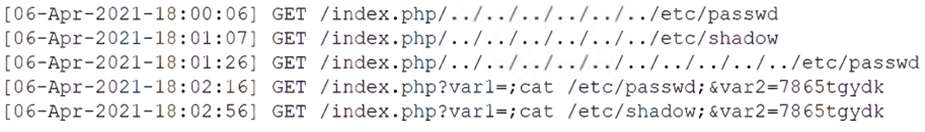
Which of the following explains these log entries?
A. SQL injection and improper input-handling attempts
B. Cross-site scripting and resource exhaustion attempts
C. Command injection and directory traversal attempts
D. Error handling and privilege escalation attempts

Which of the following explains these log entries?
A. SQL injection and improper input-handling attempts
B. Cross-site scripting and resource exhaustion attempts
C. Command injection and directory traversal attempts
D. Error handling and privilege escalation attempts