While reviewing the wireless router, a systems administrator of a small business determines someone is spoofing the MAC address of an authorized device. Given the table below:
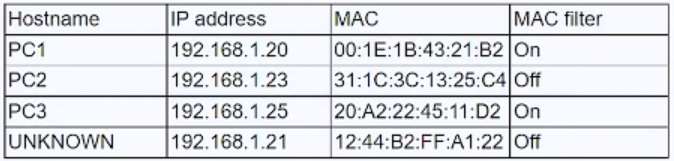
Which of the following should be the administrator's NEXT step to detect if there is a rogue system without
impacting availability?
A. Conduct a ping sweep,
B. Physically check each system.
C. Deny internet access to the "UNKNOWN" hostname.
D. Apply MAC filtering.

Which of the following should be the administrator's NEXT step to detect if there is a rogue system without
impacting availability?
A. Conduct a ping sweep,
B. Physically check each system.
C. Deny internet access to the "UNKNOWN" hostname.
D. Apply MAC filtering.